The sad truth is that ransomware is not going away any time soon. From affiliate models to double extortion to supply chain compromises, attackers have been busy honing their craft and getting creative. In honor of the second ever Anti-Ransomware Day – a date that coincides with the “peak” of the WannaCry attacks four years ago – I wanted to look at the most interesting developments in ransomware since that fateful week.
Business plans for ransomware gangs 101: the affiliate model
Pioneered in 2016 by the Petya and Cerber gangs, the “ransomware as a service” affiliate model is where we are right now, with big-name operators such as REvil, CONTI, and Ryuk taking this approach.
With ransomware as a service, the gangs build, own and manage the ransomware and ransoms, but they aren’t always responsible for the initial breach into the target organization. This is where affiliates come in.
Affiliates are recruited to join the fringes of the ransomware gang. They’re not core members, but a network of grunts who are given custom copies of the code and must find their own way into their target organization. If the breach and deployment is successful, the affiliate will receive a share of the payout. They can profit from an attack, but they don’t need the technical skills to actually build and manage the ransomware itself.
Becoming an affiliate is not as simple as turning up in a dark web forum and saying “hey, I want to use your ransomware please”. Some of these gangs will hold interviews and ask for proof of past experience before working with an affiliate. Others will only accept affiliates that they have invited to join them.
It’s also worth noting that not all ransomware groups operate under this model. While it can be a fairly lucrative, “easy” way for the gangs to make money, some groups want to maintain greater anonymity and control over their tools and where they are deployed.
The double extortion method
Ransomware is not new. Most – hopefully all – large organizations know what it is and how to prepare for an attack. They also know that the crypto ransomware groups employ is almost always well implemented, so if their files are encrypted, they’re probably not going to be able to decrypt them. As such, organizations are often forced to rely on backups. Being able to recover from backups can be the difference between having to give in to a ransom demand and continuing with business as usual.
Naturally, ransomware gangs are aware of this and have devised another way to force their victims to pay: take a copy of the data before encrypting it.
With a copy of the data now in the hands of the bad guys, it doesn’t matter if you have good backups to recover from. The dynamic shifts and the ransom demand changes: instead of ‘pay up to get access to your files’, it’s now ‘pay up or we’ll make everything public’. And unfortunately, there’s not much that can be done to circumvent this issue.
Depending on the nature of the organization and the data it holds, this could be hugely damaging to the business, its users and customers. It could see the release of highly personal and sensitive information, including medical records, mental health records and financial data.
Ransomware groups are often loud and proud about what they’ve been up to, compounding the risk. They run their own leak sites where they publicly name and shame their victims, and there’s absolutely no guarantee that the data will be deleted once the ransom has been paid. And the risk of a data leak places organizations into yet another minefield, as legislation like GDPR in the EU means they could be hit with large fines by the regulators.
We saw a sharp increase in double extortion ransomware attacks last year. With groups like Netwalker, Doppelpaymer, and REvil using it liberally, this trend will likely continue, as other groups will be tempted to adopt the same practice.
The rise and fall of ransomware operators
Ransomware operators don’t tend to last long. In recent years, we’ve seen several high profile groups announce that they’re downing tools and officially retiring. Maze, the gang known for introducing the double extortion method we discussed above, officially retired on 1 November 2020, with a public announcement that would make our copywriters shed a tear:
“Maze Team Project is announcing it is officially closed. All the links to out project, using of our brand, our work methods should be considered a scam.”
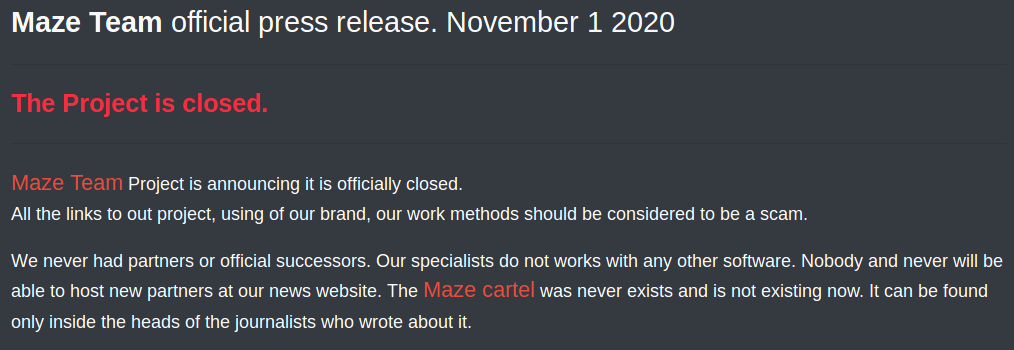
When the groups publicly announce their retirement, it’s often surrounded by pomp and ceremony. They paint themselves as heroes and feign remorse for their actions, pretending they’ve made the world a safer place by releasing the decryption keys for free. Too little, too late. The damage is done. Even with the keys in the possession of the victims, recovery is still an arduous and expensive process.
When these gangs ‘retire’, the affiliates that were working for them just move to the new kid on the block. Sadly, history has shown that there is always someone willing to step in and pick up where the old group left off.
Supply and demand
It’s always hard to predict, but something we will probably see more of is supply chain compromise used to deliver ransomware. We’ve seen a lot of recent activity, with nation-state groups reportedly using the supply chain to compromise victims. If ransomware operators can achieve the same, they could deploy ransomware to large organizations that have much tighter security controls in place.
As defenders, we are on the front line. When a zero-day or critical exploit is released, attackers, ransomware groups and their affiliates are quick to move against it – but we need to be quicker. If we can block it or detect it early enough, we may be able to limit the damage and make it significantly easier to recover.
When it comes to supply chain compromise, the difficulty will be spotting bad behavior in software you should trust. This is all about knowing your environment and how your users operate, so you can identify suspicious behavior in the precious moments leading up to a ransomware attack. Enumeration, lateral movement, and credential harvesting are well-documented TTPs that attackers use before deploying ransomware.
What’s next?
We should expect much of the same in the coming years. The ransomware methodology has been refined and established over the last half-decade, and cybercriminals have found it to be highly effective. Unless we make significant policy changes to either force victims not to pay, or to enable law enforcement agencies to pursue ransomware operators regardless of nationality, ransomware attacks will continue.
As pessimistic as it sounds, with ransomware, it’s more a question of “when” than “if”. As such, every organization would do well to have a crisis response plan in place, and to regularly test and update that plan according to new methods, actors and business priorities. When it comes to the crunch, you need to be prepared to act.

Kev Breen,
Director of Cyber Threat Research, Immersive Labs
@kevthehermit


