Welcome to Immersive Labs
Immersive Labs online exercises form part of the application process for CyberFirst. Immersive Labs will enable you to improve, measure and evidence your cyber security capabilities, the exercises you undertake should be fun, engaging and sometimes challenging.
Register for CyberFirst
There are lots of different areas to choose from and you’ll be given more information once you’re in the platform. First of all though, you need to register, even if you have previously used Immersive Labs or completed practice exercises you will need to follow the instructions below to create a new registration especially for your CyberFirst application.
Account Creation
Please make sure that you:
Use the same email address that you have used throughout the CyberFirst application process.
Choose a strong password by combining three random words
Read and agree to our Terms of Use and Privacy Policy.
Use the code CyberFirst2025


Account Verification
Keep an eye on your inbox for a confirmation email. You will receive a verification email to your address to complete the registration. When you confirm your email address you will be asked to complete your profile.
Complete Your Profile
For your security and to ensure an anonymous recruitment process we don’t want you to input your personal information into your profile, please follow the instructions below very carefully and input your details as outlined below.
If you don’t follow this advice your efforts won’t count and the work you do will be invalidated.
Name - Surname - Username
Please input CF followed by your candidate ID number (your candidate ID number is the number that is at the top of all emails from the recruitment team) e.g. CF1234567
Timezone
Please select the correct timezone to allow your results to be reported accurately.
Let other people see my details
Don’t worry about the tick box, no one else will be able to view your details or activity. If you make a mistake, you can adjust all of these settings in the ‘Profile’ section once you’ve logged into the platform.
.webp)

Role
This next section will not count towards your application, it is a standard part of the Immersive Labs platform where we try and capture more about an individual’s cybersecurity experience, however, we know that most applicants to CyberFirst are unlikely to have any formal work experience and simply have an interest in the area.
We assume that you do not currently work in cybersecurity, if that is the case select ‘Other Non-Technical Roles’
We also assume that you will not have any work experience in cyber security, if that is the case select ‘0’
Finally if you are not currently working select ‘none of the above’
Priority Areas
Please choose the areas of cybersecurity that you are currently interested in. This information does not have a bearing on your CyberFirst application; it simply helps us offer some appropriate Labs to you.
Skills
Please select your skill level in each of the 3 skill areas presented. We do not expect CyberFirst candidates to be above an Advanced Beginner level. This information does not have a bearing on your CyberFirst application; it simply helps us offer some appropriate Labs to you.
Your First Activity
You will be recommended a number of labs based on the information that you have provided. You should skip these for now and go straight to the Launchpad.
Your Launchpad
This is where you will land each time you enter the Immersive Labs platform. Here you can find all of the content that has been assigned to you.

Assessments
You have been assigned a Decision Making Assessment and 9 Cybersecurity Roles. Click “View All” to see the complete list.
Decision Making Assessment
Into the Unknown – In this exercise, you’ll be presented with a number of different scenarios, designed to cover a range of technical and social challenges.
Each scenario will have several decision points where you’ll need to choose which action should be taken. The scenario and case files provide all the information you need.
You don’t need to use the internet or additional resources to complete the exercise.
There is no time limit to completing this exercise. However, you must complete the exercise before 23:59 GMT on 8th December 2025.
Cybersecurity Roles
You have been assigned a Decision Making Assessment and 9 Cybersecurity Roles. Click “View All” to see the complete list.
The study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. Candidates with an interest in maths may find this specialism of interest.
A role that involves responding to reported suspected cyber security hacks and incidents. It is a people facing role, as well as a bridge between the technical and non-technical community. Candidates with an interest in psychology, sociology, English, statistics, maths, communication or media studies may find this specialism of interest.
Relates to uncovering what digital clues have been left on systems by suspected hackers, as well as preserving them as proof of evidence. Candidates with an interest in history, geography, investigations or research and problem solving may find this specialism of interest.
Software and IT solutions are where people interact with the technology, meaning a product needs to be developed with people, security and technology together. Secure development is the ethos by which solutions are developed securely, as well as tested and made ready for their intended customers. There are many roles under this heading. Candidates with an interest in business, networking or software development may find this specialism of interest.
This role works to ensure a software solution is secure from start to finish, including how people with a variety of roles interact with it, such as users and administrators. Candidates with an interest in programming, networking, maths, English or communications may find this specialism of interest.
This role involves collecting and analysing information to detect suspicious behaviour on a network. Defining the behaviour that triggers alerts and acting on them ensures a system is protected from unauthorised access. Candidates with an interest in networking, maths or programming may find this specialism of interest.
This role is the process by which IT solutions are researched, tested and documented to ensure they are adequately protected. Candidates with an interest in history, maths, geography, English, networking or programming may find this specialism of interest.
This is the role that allows systems to be looked at as a whole, and not just at the technical level, to best defend them from hackers. Candidates with an interest in history, maths, geography, English, networking, programming may find this specialism of interest.
This is a research, analysis and reporting role, on the various threats being posed to IT implementations. Candidates with an interest in history, maths, geography, English, networking or programming may find this specialism of interest.
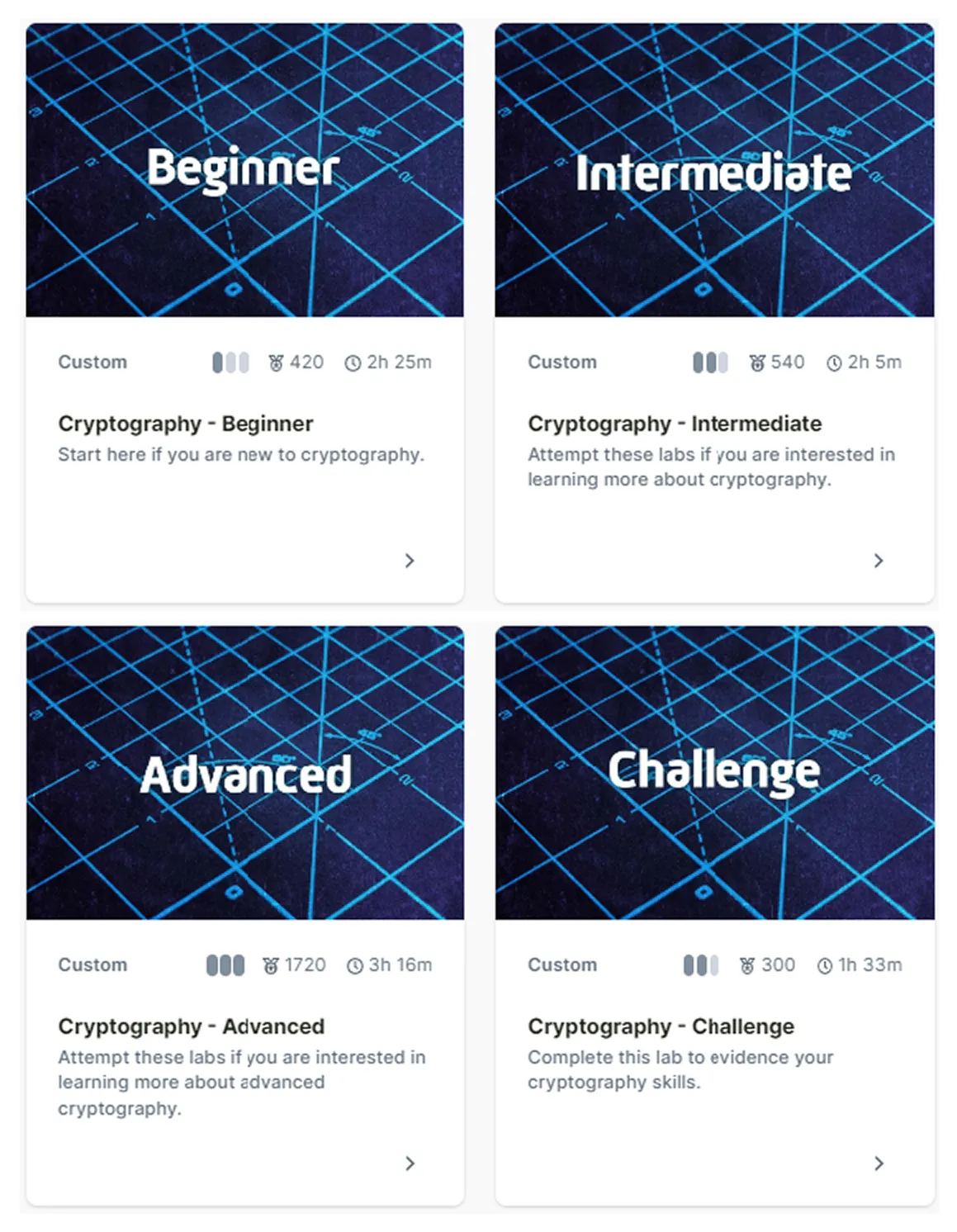
Labs
Each role contains a number of labs, which range from beginner to advanced difficulty, as well as a challenge lab. You are encouraged to complete 5 challenge labs in five different roles.
The challenge labs are the most testing labs in each of the 9 cybersecurity roles. By completing a challenge lab you are evidencing that you have some of the skills required in that work role. If you think that you already possess those skills, you should try to complete the challenge lab straight away, but if you want to learn more about the role, or brush up on your skill, why not try the related Beginner, Intermediate and Advanced labs first?
Don’t worry if some or all of the challenge labs are too tricky for you to complete, we are also looking for candidates who are eager to learn about new areas of cybersecurity. If that’s you, just try and complete as many labs as you can, at the highest difficulty that you can manage as that gives us an understanding of your aptitude even if you haven’t completed a challenge lab.
You may need to use the internet or additional resources to complete some labs.
The deadline for lab completions is before 23:59 GMT on 8th December 2025.
Knowledge Base and Support
Please use the Knowledge Base for more information about Getting Started with Immersive Labs and to read our FAQs.
You can also contact support using the Contact Us link if you experience any technical difficulties.





.svg)


.webp)


