CrowdStrike: The Impact of Faulty EDR and ELAM Drivers

CrowdStrike BSoD Chaos:
A Critical Lesson in Cyber Resilience
Banks, stock exchanges, airports, and other major enterprises worldwide are grappling with unexpected denial-of-service conditions caused by widespread Blue Screen of Death (BSoD) events in their Windows environments. These crashes are severely impacting critical infrastructure, leading to operational disruptions and financial losses.

Understanding the Blue Screen of Death (BSoD) Crisis
A BSoD occurs when a kernel-level crash or memory error forces Windows to shut down abruptly. This widespread issue appears to be linked to the CrowdStrike Falcon Endpoint Detection and Response (EDR) agent, specifically its Early Launch Anti-Malware (ELAM) driver.
The Role of EDR and ELAM in Windows Security
EDR products like Falcon use specially signed Microsoft drivers to gain access to event-tracing feeds within the operating system, enabling the detection of advanced threats while remaining difficult for attackers to evade. ELAM driver signing is exclusive to companies that create EDR products, with Microsoft granting access only after a degree of trust and verification.
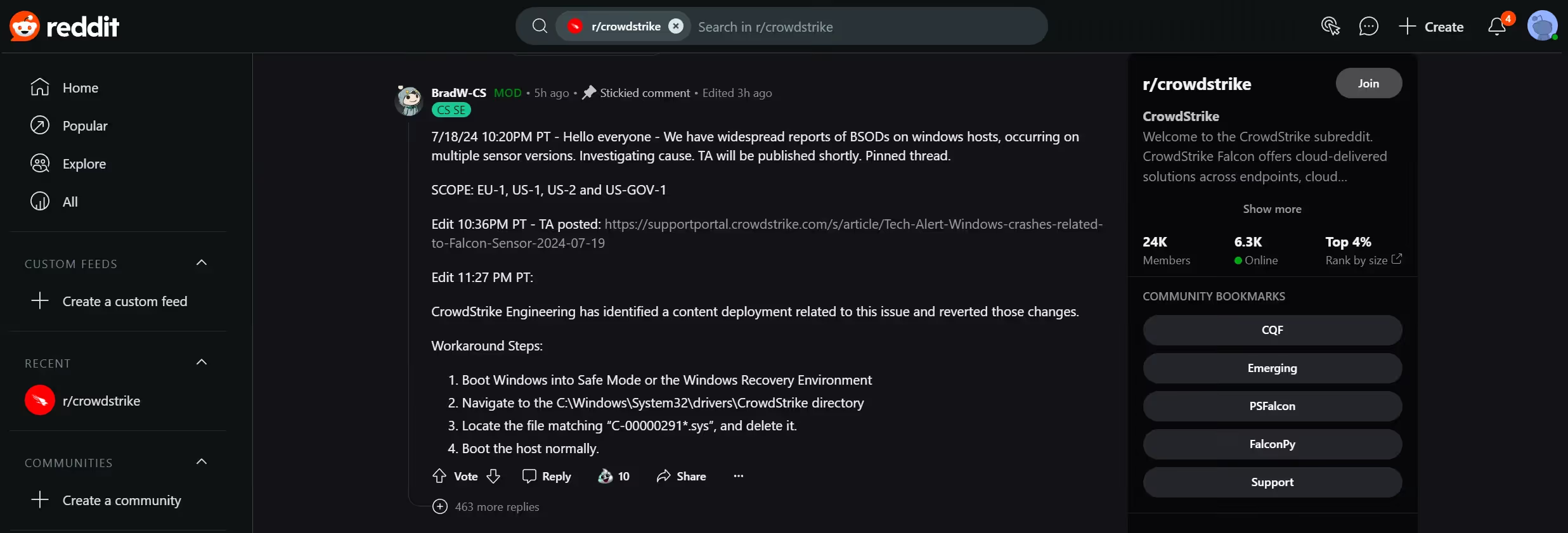
No Quick Fix:
The Challenge of Removing the Faulty Driver
At the time of publication, there is no automated or remote method to remove the faulty ELAM driver due to its early-launch nature. Fixing the issue requires users to boot into Windows Safe Mode with ELAM driver loading disabled and manually delete the problematic file. This approach demands physical access to each affected machine and is particularly challenging for cloud-based systems, requiring deeper knowledge of underlying infrastructure.
Falcon’s Reputation: A Double-Edged Sword?
CrowdStrike Falcon is one of the most widely used and highly regarded EDR products on the market. Security professionals trust Falcon to protect networks from sophisticated cyber threats, giving defenders the edge they need to detect, prevent, and respond to attacks effectively. Typically, CrowdStrike employs rigorous testing protocols before rolling out updates, ensuring compatibility across multiple Windows versions. However, in this case, that process appears to have failed.
What Went Wrong? The Unanswered Questions
It remains unclear whether the issue was caused by a fault in the driver code or an unanticipated, undocumented change in the Windows operating system that CrowdStrike could not have foreseen. What is evident, however, is that Falcon’s widespread adoption has made it both a crucial security asset and a potential single point of failure, leading to severe global disruptions.
This incident highlights the critical need for stringent testing and quality assurance in cybersecurity products, especially those operating at the kernel level. EDR and ELAM driver updates must undergo extensive validation to prevent catastrophic failures that can cripple businesses worldwide.
Balancing Security and Control in Product Updates
This event raises an important question: Should security product updates be automatically applied to ensure systems remain protected against evolving threats, or should organizations have greater control over update deployment to allow for internal testing? Striking the right balance between security and stability is crucial for minimizing risk.
Prepare for the Next Crisis: Immersive Labs Crisis Sim
For Immersive Labs Crisis Sim customers, the Unforeseen Consequences exercise is now available. This Crisis Sim immerses security teams in the first hour of a similar global event, allowing them to test their response strategies in a high-pressure environment.
To learn more about the Immersive Labs platform, including our Cyber Crisis Simulator, schedule a demo today














Ready to Get Started?
Get a Live Demo.
Simply complete the form to schedule time with an expert that works best for your calendar.





.svg)
.webp)









.webp)


