Cyber Crisis Simulator: Digital Tabletops for Global Teams
Go beyond traditional tabletop exercises and put your teams into dynamic crisis simulations to maximize executive training schedules.
- For boards, executive management, and crisis management teams
- Pre-built with engaging storylines and media or completely customizable
- Capture insightful data and actionable results
- Build muscle memory for better decision-making
- Browser-based for scalability


Dynamic
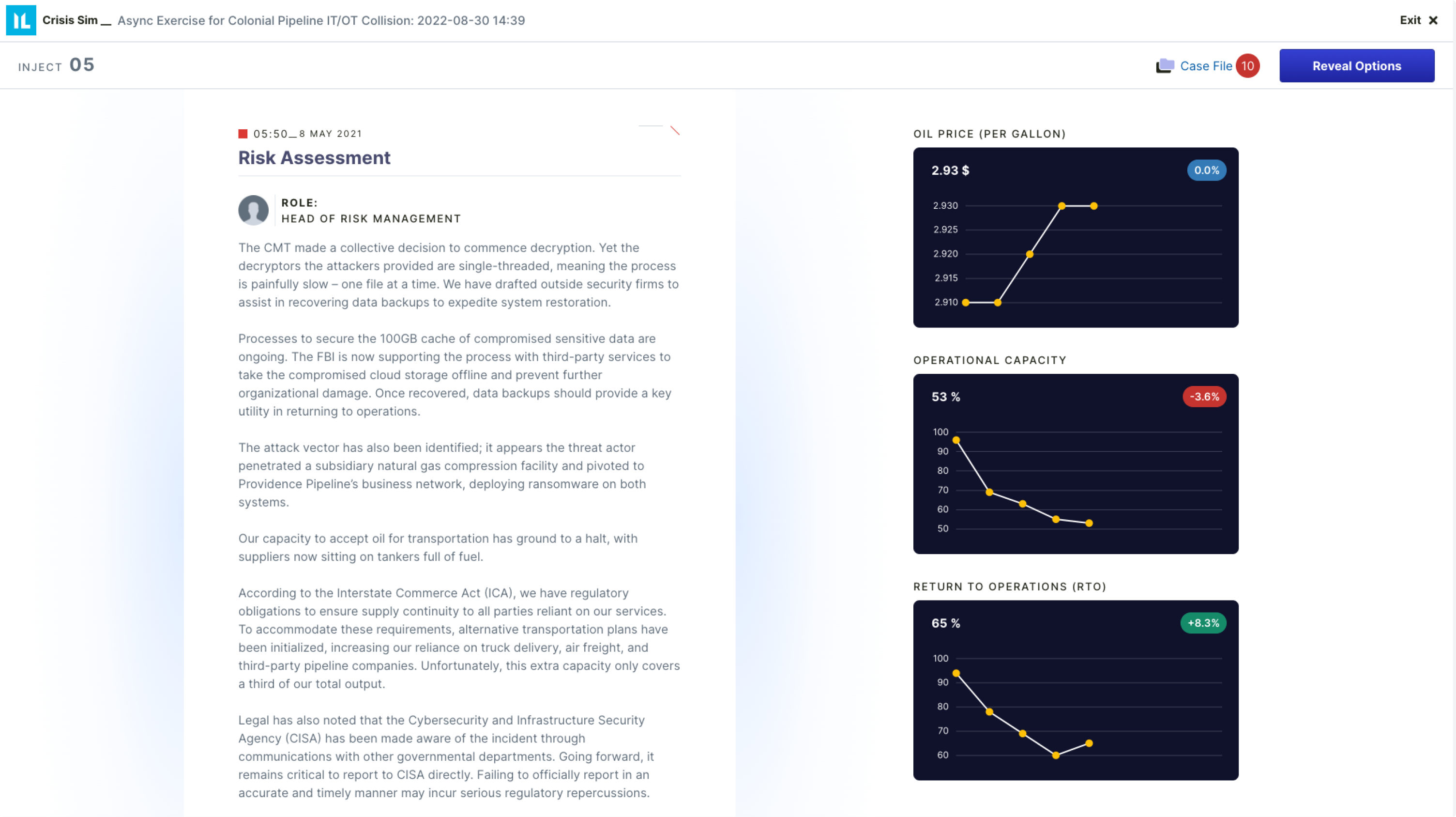
Unlike linear tabletop exercises, our simulations reflect how a crisis unfolds in the real world – your teams will never know what problem they’ll face next. Continually test and prepare teams using the latest crisis scenarios.
Customizable
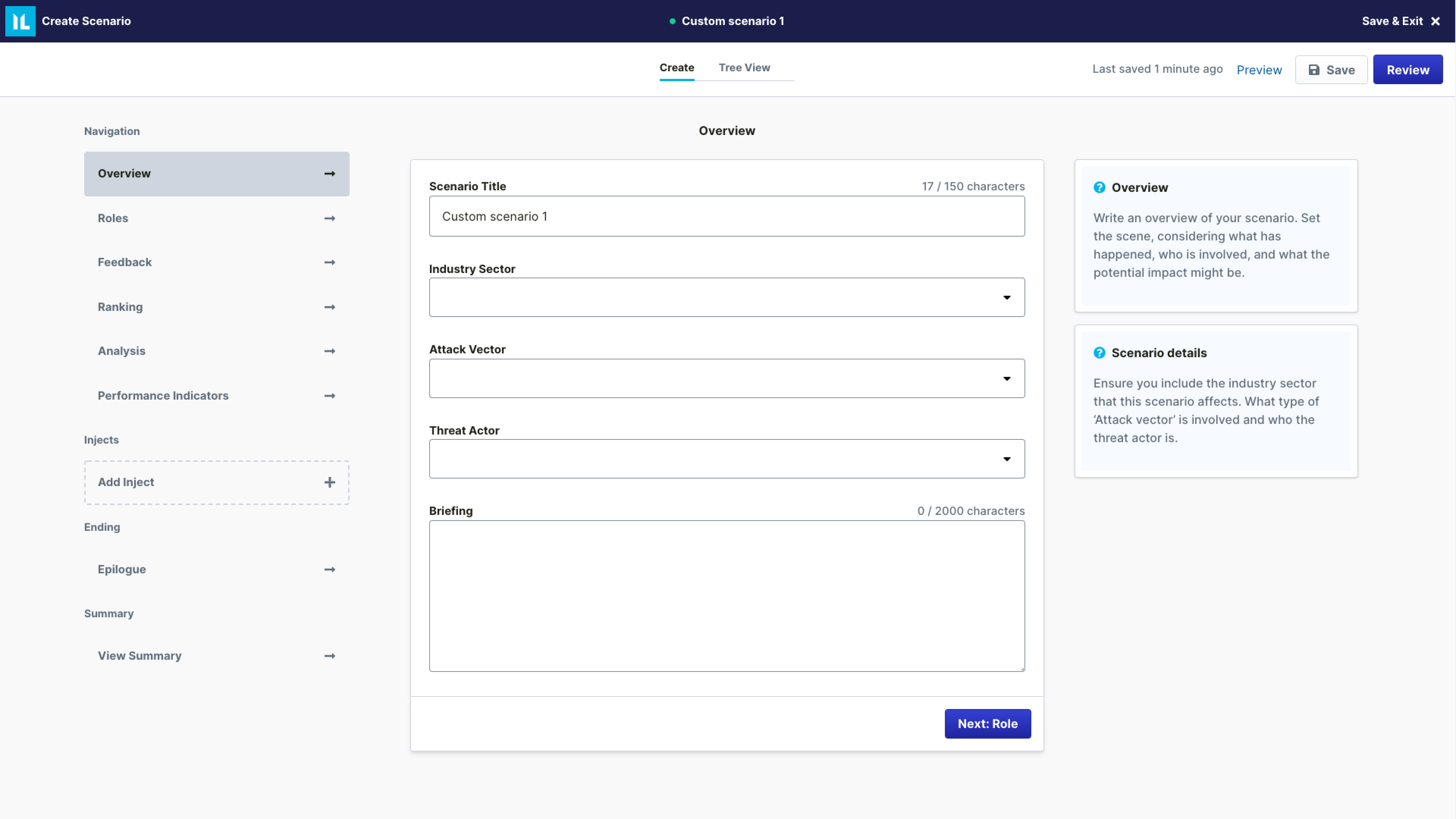
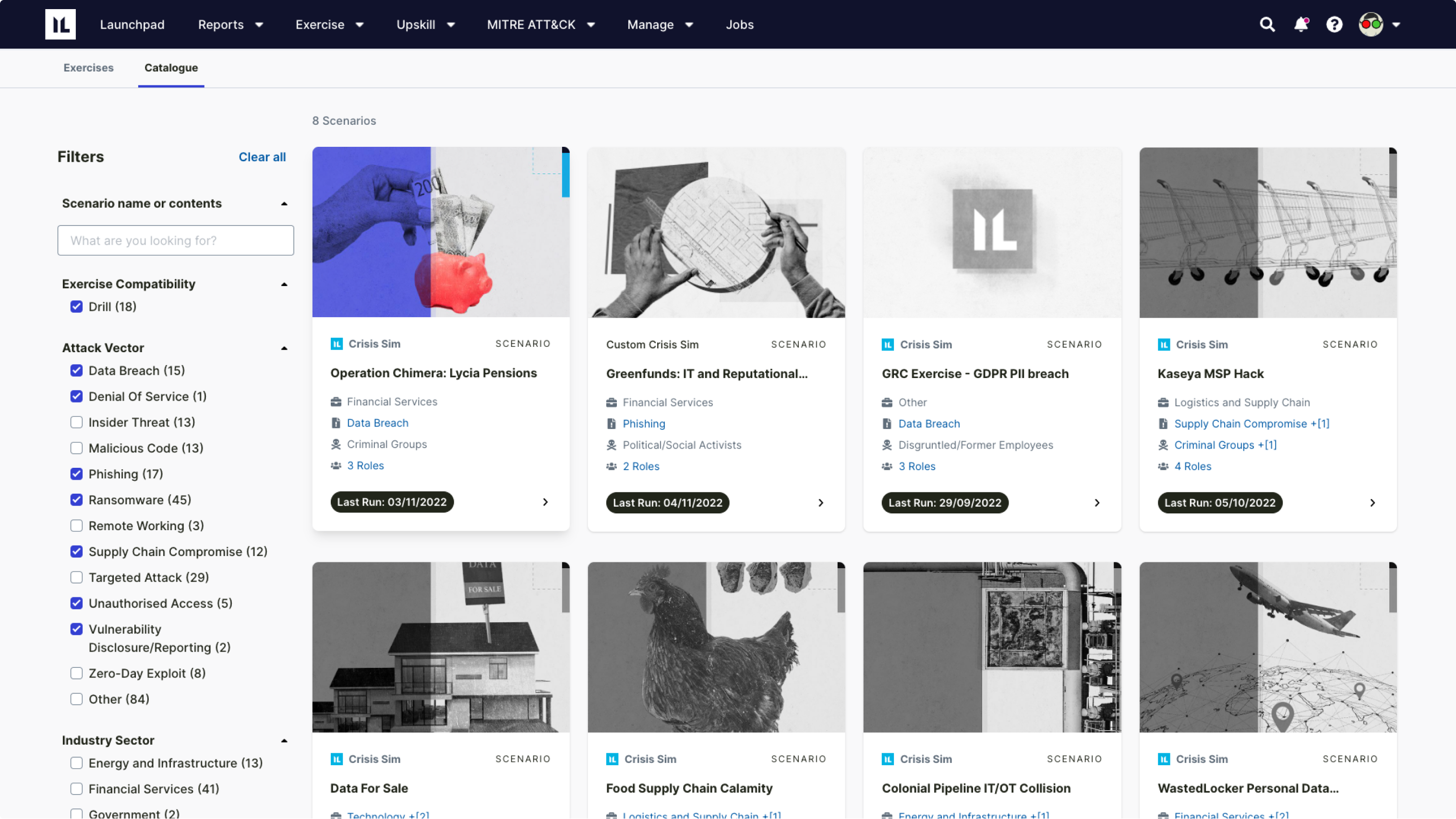
Out-of-the-box scenarios deliver exercises for numerous crisis types and industries. But you can also customize scenarios by adding decision points (injects) or building a completely new exercise to address specific areas of your organization – ensuring continuous improvement.
Data-Driven
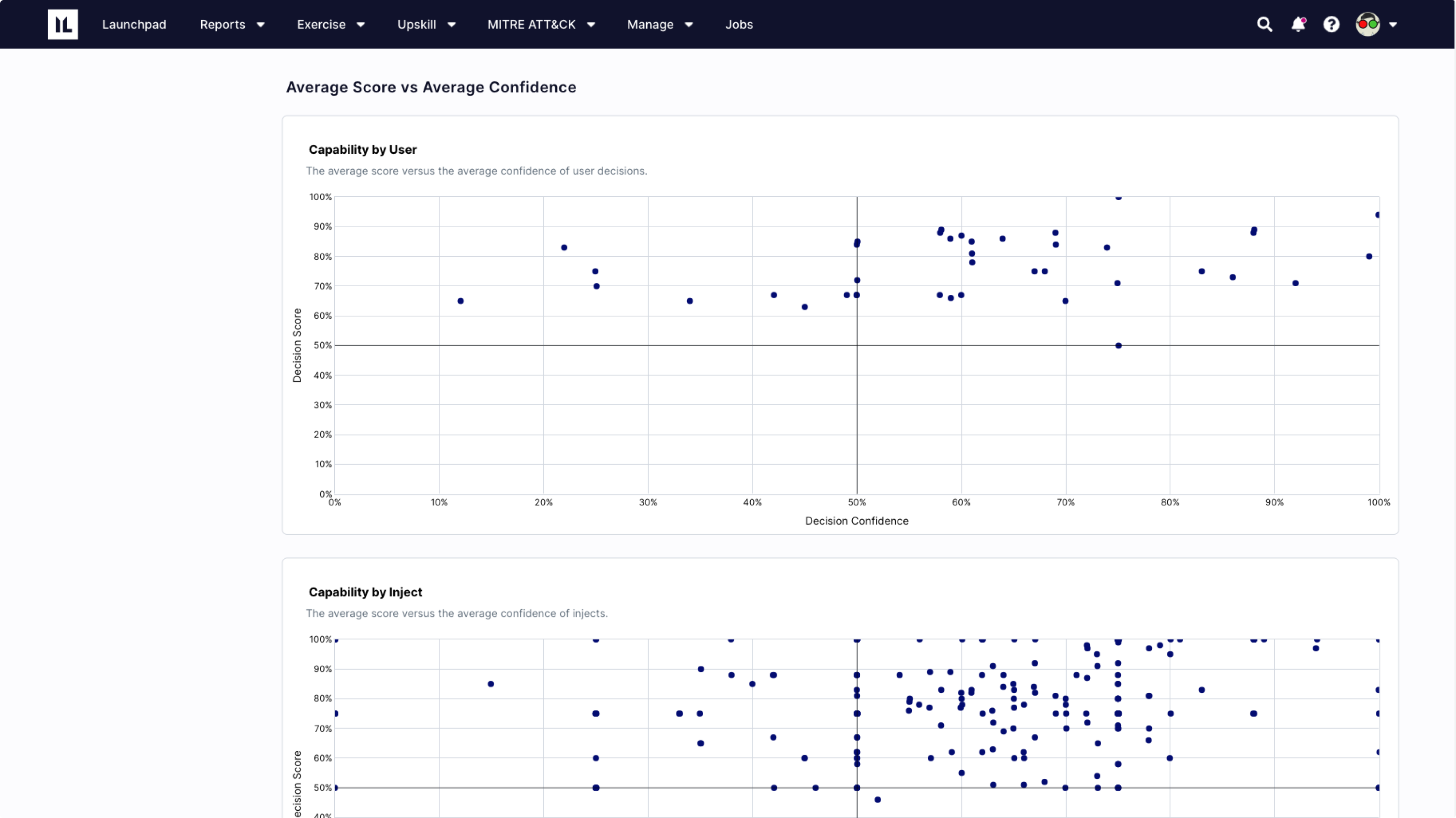
Exercise results are scored for individuals and the team participating – including the confidence level for each answer. The results help prove an organization will be ready for a real-life crisis (or that more exercising is required). Track individual and team performance over time to prove readiness and enhance decision-making when faced with a real-world crisis.
Global Reach
Browser-based delivery removes the logistical burden of in-person tabletop exercises. No matter where you’re located, Crisis Sim support for scalability makes it perfect for globally-dispersed teams.
Frequently Asked Questions
Realistic simulation of current threats is the only way to test and improve response readiness and ensure that an actual attack’s impact is minimized. Immersive Labs’ innovative platform, combined with Kroll’s extensive experience, provides the closest thing to replicating a real incident within a safe virtual environment.

