Lessons from the Latest CISA KEV Additions

The Cybersecurity and Infrastructure Security Agency (CISA) recently added five vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, including a critical 2017 remote code execution flaw in Jenkins (CVE-2017-1000353).
These additions have demonstrated that the biggest threats aren't new zero-days, which can take down any system, as is often portrayed in the media. They're often the old, known, and unpatched vulnerabilities.
The KEV catalog
The CISA Known Exploited Vulnerabilities (KEV) catalog is a curated, authoritative list of security flaws that have been observed being actively exploited by malicious actors in the wild.
The catalog’s primary purpose is to help organizations prioritize their vulnerability management efforts. Instead of focusing solely on theoretical risks or severity scores, the KEV catalog provides intelligence on immediate threats that have been used by threat actors in the wild. It allows security teams to allocate resources to patching the specific vulnerabilities that pose a current and tangible threat to their networks and systems.
This focus on proven, real-world exploits makes it an essential tool for cutting through the noise of countless disclosures and enhancing an organization's defensive posture against the most likely attack vectors.
At Immersive, we like this list because it shows companies where to prioritize. We aim to address many of these vulnerabilities in our CTI labs to ensure security teams understand the real-world impact these vulnerabilities have on systems.
The continued threat of older vulnerabilities
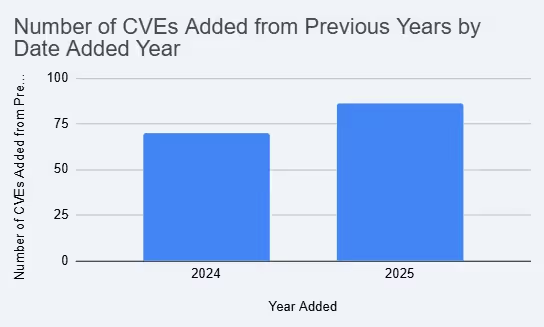

As of October 10, 2025, 196 vulnerabilities have been added to the KEV catalog. 86 are from previous years; 110 are from 2025.
That means 43% of vulnerabilities seen in the wild by CISA are from previous years, which organizations have had ample time to patch. As you can see from 2024, the number of new vulnerabilities and older, known ones added was largely the same.
This raises some important points:
- Vulnerabilities from previous years are more likely to have proof-of-concept or exploit code released, due to researchers often examining older vulnerabilities.
- Zero-days don’t account for as many in-the-wild hacks as the industry might think.
- These vulnerabilities from older years are usually safer to attack, as they’re less likely to be managed by organizations.
- Hackers will often seek the lowest-hanging fruit to gain access to a system, which isn’t necessarily the new, shiny exploit.
The economics of hacking
Attackers follow the path of least resistance because it offers the best return on investment. Developing a new zero-day exploit is expensive and time-consuming – why do that when you can use a publicly known vulnerability or simply trick an employee?
Modern defenses have made purely technical exploits harder. This has forced a strategic pivot to simpler, more reliable methods for attackers:
- Proven vulnerabilities: Flaws like ProxyLogon are attacker favorites. The software is everywhere, the exploit is reliable, and it has been proven time and time again to be found in organizations’ networks.
- Social engineering: Groups like Scattered Spider bypass technical controls entirely. They manipulate people through MFA fatigue and vishing attacks to gain access. They hack the person, not the code.
Your real to-do list
Obsessing over zero-days while neglecting basic cyber hygiene is a flawed strategy. To build a resilient defense, focus on what actually stops attacks.
- Prioritize the KEV catalog: Treat CISA's list as your immediate patching priority. These are the vulnerabilities being exploited in the wild right now.
- Train for reality: Move beyond basic phishing tests. Drill your workforce on modern social engineering tactics to build genuine resilience against human-targeted attacks.
- Master the fundamentals: Solid asset management, vulnerability scanning, and secure configurations aren’t exciting, but they’re the bedrock of effective cybersecurity.
Explore more in our latest labs
We’ve recently released two labs on the known CVE-2017-100053 vulnerabilities – you can choose the Defensive or Offensive option:














Ready to Get Started?
Get a Live Demo.
Simply complete the form to schedule time with an expert that works best for your calendar.





.svg)
.webp)









.webp)


