Cyber Threat Protection & Prevention

Imagine a castle so substantial that no army could ever breach its walls. But what if the guards inside, entrusted with the keys, left the gates wide open? This is the reality many organizations face today in their continuous battle against cyber attacks. Organizations pour vast resources into sophisticated technological defenses, yet often overlook a critical vulnerability–their people.
What is a cyber threat?
The National Institute of Standards and Technology defines cyber threats as:
Any circumstance or event with the potential to adversely impact organizational operations, organizational assets, or individuals through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service.
Cyber attacks are on the rise, threatening infrastructure, supply chains, brand reputations, and revenues. Of these breaches, over 60 percent involve the human element. Given this statistic, it is evident that technology alone is not a viable solution. To confront new and emerging threats, workforces and leaders need increased visibility into areas of weakness and practical strategies for filling these gaps. To illustrate how organizations can prepare their people to better combat cyber threats, we sat down with Christopher Porter, CISO at Fannie Mae, and Ed Amoroso, CEO and Founder at TAG Cyber, to discuss actionable solutions on our ‘Putting People at the Center of Cyber’ webinar.
Cyber threat challenges
The Identity Theft Resource Center (ITRC), a non-profit dedicated to empowering individuals and businesses against identity theft, recently released its 2024 Data Breach Report, and the findings reveal a concerning trend: data compromises are at near-record levels, impacting individuals and businesses on an unprecedented scale.
The report shares that in 2024, the U.S. experienced a staggering 3,158 reported data compromises, which resulted in over 1.3 billion victim notices. To put that into perspective, it's the equivalent of every single adult in the country receiving six data breach alerts.
While five "mega-breaches" contributed significantly to these numbers, many of these incidents could have been avoided if their workforces had been empowered with critical cyber capabilities. Even more concerning is that a significant volume of these breaches stemmed from preventable causes, such as phishing attacks, weak passwords, and a failure to implement multi-factor authentication (MFA). The report estimates that at least 196 of these compromises could have been prevented through the effective implementation of basic cybersecurity practices.
When we consider what threats organizations face, Kev Breen, Director of Cyber Threat Research at Immersive, explains, "The thing that's really quite terrifying is that we've known about things like phishing attacks for decades, yet those are still successful today. And then we have the other side of the spectrum where we have really advanced threat actors with really custom malware, custom TTPs stuff that's never been seen before and they're just as effective as phishing attacks."
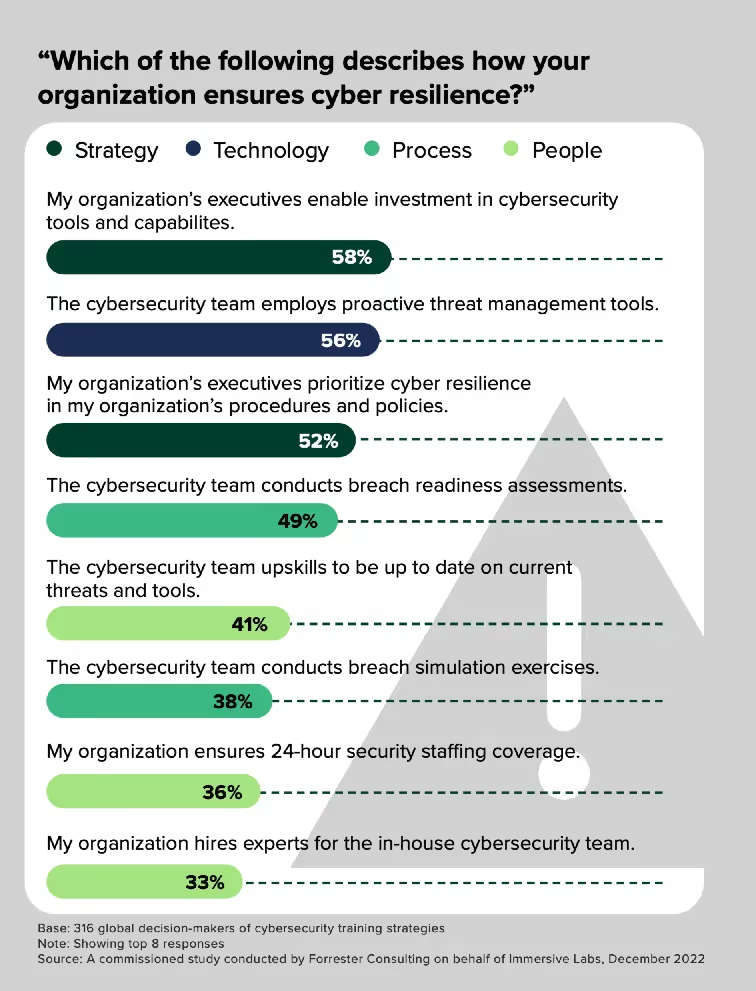
Main cyber resilience gaps
A recent Forrester Consulting study commissioned by Immersive found that the main challenge facing cyber resilience is insufficient security expertise. The key takeaway for leaders? Invest in your people and their cyber skills.
Cyber threat protection: technical safeguards
Firewall
Your organization's defense begins at the perimeter with firewall technology, standing guard like sentinels at the castle gates. These vigilant guardians constantly monitor all traffic attempting to enter or leave your network. They carefully examine each digital visitor, allowing trusted messengers to pass while blocking suspicious characters. By creating clear boundaries between your trusted internal kingdom and the potentially dangerous outside world, firewalls ensure that only authorized communications can cross the threshold.
Antivirus solutions
Antivirus solutions act as roaming security patrols, constantly searching for intruders that might have slipped past initial defenses. These guardians use two primary methods to identify threats: they match suspicious code against known criminal profiles (signature-based detection) and watch for suspicious behavior patterns that might indicate malicious intent. Working tirelessly around the clock, they conduct both real-time surveillance and scheduled comprehensive sweeps of your entire digital domain, neutralizing threats before they can cause harm.
Password management
Access to your most valuable resources is controlled through sophisticated password management systems—the equivalent of secure vaults with complex combination locks. Rather than relying on simple keys that can be easily duplicated, these systems create and store elaborate combinations unique to each doorway and user. For especially sensitive areas, multiple verification methods are required (multi-factor authentication), similar to needing both a physical key and a biometric scan. The system automatically updates these combinations regularly and monitors for any signs that access codes might have been compromised.
Data encryption
Data encryption serves as the ultimate protection for your most precious assets. Through sophisticated mathematical transformations, encryption converts your valuable information into indecipherable code that can only be unlocked with the proper key. When sending treasures beyond your walls, end-to-end encryption ensures they remain securely locked throughout their journey. Similarly, encryption at rest means that even if an intruder somehow breached all other defenses, they would find only unintelligible scrambled content instead of valuable secrets.
Why people-centric threat prevention is critical
People are at the heart of cybersecurity. Effective security is not just about firewalls and sophisticated algorithms, it is about empowering every individual within an organization to be a security champion. Even the strongest castle walls are useless if the guards aren’t adequately trained to protect them. A people-centric approach recognizes that employees are not just a potential vulnerability, they can also be your strongest security asset.
Building a resilient organization where everyone feels empowered to take charge of their security posture leads to:
- Reduced risk of breaches: Educated employees are less likely to fall victim to attacks, minimizing the chances of a successful breach.
- Improved incident response: When everyone knows their role in an incident, the response is faster and more effective, limiting damage.
- Enhanced employee engagement: When employees feel trusted and valued as part of the organization’s security solution, their overall engagement and morale improve.
- Stronger organizational reputation: Protecting customer data is a core expectation, not a luxury. Demonstrating a strong cybersecurity posture is essential for maintaining trust and avoiding severe reputational damage following a data breach. Failure to adequately safeguard data will lead to customer distrust and potential loss of business.
As Dave Spencer, Director of Technical Product Management at Immersive, reminds us, "The threats haven't changed. The threats are still the same. It's still people fishing their way in. It's still people executing code on boxes. It's still people stealing secrets or just encrypting stuff. The only real difference now is how they go about it." What has evolved are the tactics used after a compromise, which have become more sophisticated, especially with ransomware becoming an established business model.
How to improve your cyber threat prevention
1. Build a culture of security
Cybersecurity shouldn't be an afterthought or a task left solely to the IT department. It should be woven into the very fabric of your organization's culture. Encourage open communication so employees feel comfortable reporting suspicious emails or activities without fear of blame. Leaders should set the tone by demonstrating their commitment to security practices.
Ben McCarthy, Lead Cyber Security Engineer at Immersive, warns about the dangers of weak security awareness across the organization.
"A weak security culture can be devastating to an organization because it means that people just aren't upskilled. They don't understand what a bad phishing email looks like. And they could end up going down the rabbit hole of responding to these attackers and giving them initial access to networks. “
What’s worse in this scenario? Your people not reporting the phishing email they clicked on because they're worried that they're going to get a slap on the wrist while actually that’s exactly what security teams want.
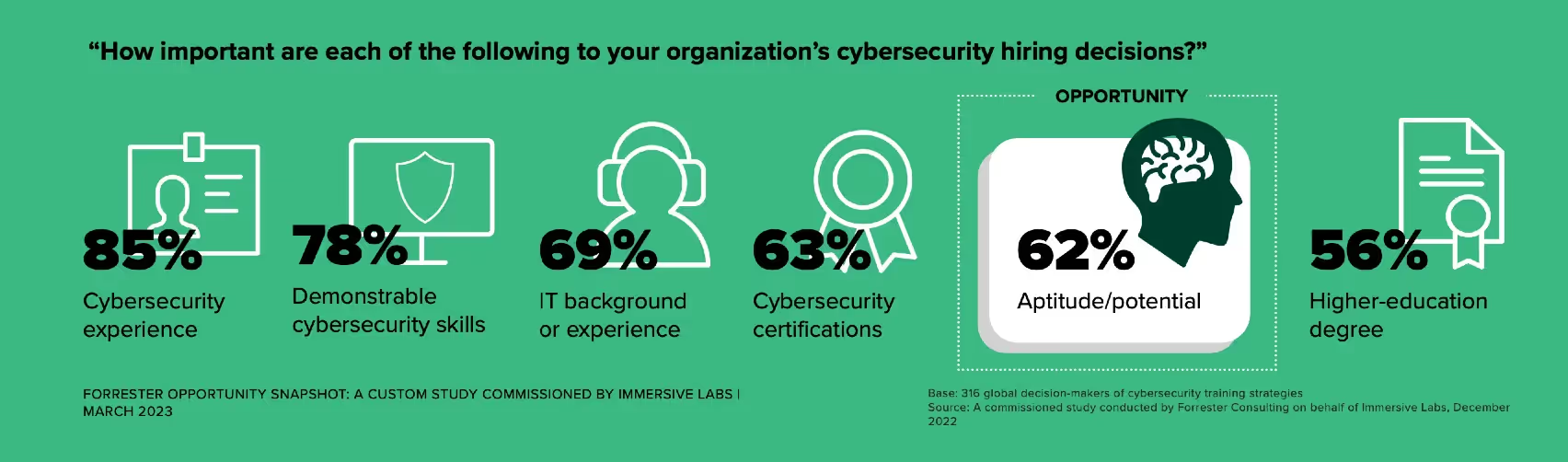
2. Prioritize potential
When hiring, don’t be afraid to prioritize potential over credentials. Existing hiring practices often overlook individuals with the aptitude to thrive in cybersecurity roles, as they frequently don’t have the proper certifications. This exclusionary process can create a barrier to entry for many job seekers and limit diversification of talent.
Breen emphasizes the importance of prioritization: "When it comes to prioritization what's most important is understanding your organisation, the technology you have, the threat profile you have, what are the important things to you, and then from there, it's just playing the game. Understanding that when all these things come in, it's up to your security teams to go, 'Actually, let me have a look at this. This is nothing'. And then it's all about pace."
3. Provide hands-on learning
Provide the people you do employ opportunities to learn new skills or sharpen their processes – and prioritize training with immediate, lasting impact. Adopt hands-on, continuous exercising through easy access to on-demand real-life cyber simulations. By providing employees with dynamic, immersive threat scenarios, organizations support skills development and growth.
Spencer emphasizes that despite all the attention on new technologies like AI, organizations shouldn't lose focus on traditional threats.
"The top threats will always come back to ransomware and phishing attacks. But we’re also becoming complacent. We’re starting to ignore them—much like the current buzz around AI. AI is no more dangerous than a phishing attack. Both can still get in, cause reputational damage, and lead to financial loss."
4. Make sure your team understands threat factors
When we look at threats that affect different types of organizations, the level of actors can drastically change. So individuals personally can be targeted a lot more by cybercrime, like low-level groups making use of quite fundamental techniques, still targeted at the individual.
Gaz Lockwood, Principle Threat Hunt Engineer, explains how different organizations face varying levels of threats based on their size and value as targets.
"As you move up the size of the organization, the level of complexity that actors bring to bear against the organization often increases. Now you still get targeted by the lower levels, but you also start incorporating more capable actors against different organizations. Then you obviously attract a larger investment from threat actors to achieve their goal."
5. Provide continuous upskilling
Bad actors never stop innovating; therefore, neither should you. Invest in ongoing training relevant to each employee's role and responsibilities. With on-demand, online cyber skills content, employees gain hands-on experience with tools, technology, and techniques that help them build and hone their skills in an ever-changing threat landscape. By enabling the constant adaptation required to be effective in cybersecurity, proactive, interactive upskilling can uplevel employees to ensure that the next breach is prevented.
For example, Breen notes: "On any given month, I think there's around 3,000 CVEs released. Most of them, not exploitable; they're real vulnerabilities, but most of them are never gonna be exploited. They're theoretical or hypothetical, don't have proof of concepts. So it's important for security teams to go 'We can't just blindly patch everything'. You have to prioritize, especially as we have more and more products."
6. Think like an attacker
Sometimes it’s best to put yourself in the shoes of the bad actors. Just so you can be a few steps ahead. Matt Parven, Principal Content Developer at Immersive, highlights the importance of understanding the adversary's perspective.
"It's really important for defenders to understand how attackers think. And I think giving people that mindset of, 'oh, this is what an attacker could do' is a really important mindset to be giving anyone in the cybersecurity industry."
7. Have an incident response readiness plan
Develop a clear incident response plan that outlines the steps to take when (not if) an incident occurs. This ensures swift action, minimizes damage, and helps you learn from mistakes. Regularly rehearse this plan to ensure everyone knows their role in a crisis.
Breen advises organizations to shift their mindset from perfect prevention to effective detection and response.
"You can invest a lot of time, a lot of energy, a lot of technology in trying to close every hole. But we've seen the number of zero days, the number of supply chain compromises. It's practically impossible to guarantee they can't get in. So don't focus on trying to close all the holes. Focus on your response when they get in."
8. Collaborate across teams
Parven emphasizes that effective security requires breaking down silos between different roles.
"When an incident happens, it doesn't matter whether you're an executive or whether you're an incident responder. It's important to work as one team. That's how you reduce your time to remediate whatever that attack or whatever that vulnerability is.’
And the immersive platform helps with that with our different Immersive One solutions like crisis simulation, our labs, and our cyber range exercises, which allow teams to come together, no matter what their level is in an organization, no matter what their role is.
It allows organizations to basically work as one team, understand how they can communicate together to get to the midst of what is happening in this environment, what is happening in this scenario.
Implement the right threat protection tools
At Immersive, we deliver challenge-based cybersecurity content developed by experts and powered by the latest threat intelligence. Our unique approach enables businesses to battle-test and evidence their workforce’s preparedness to face emerging cyber threats, moving you beyond generic training courses to interactive skills content that’s relevant to the risks you face. And best of all, it’s available entirely through the browser, so your people can up their game anywhere, anytime. To see why so many global enterprises are placing their trust in Immersive Labs, book a demo today.
Trusted by top
companies worldwide














Ready to Get Started?
Get a Live Demo.
Simply complete the form to schedule time with an expert that works best for your calendar.





.svg)
.webp)












.webp)


