Scattered LAPSUS$ Hunters: The Cybercrime Group Redefining Threats

Corporate mergers and acquisitions have long reshaped industries, pooling talent, resources, and market share into something greater than the sum of its parts. Now, cybercriminals are following the same playbook.
Three of the most notorious groups this year, Scattered Spider, LAPSUS$, and ShinyHunters, have joined forces in what analysts believe is not a passing collaboration but a permanent consolidation. The result: Scattered LAPSUS$ Hunters, a cybercrime group combining each collective’s proven tactics, techniques, and procedures into a unified threat.
Individually, each group has succeeded in breaching many organizations around the world, often tipping the industry off about their movements before starting. So, what do you do if you think this group might be attacking you and your industry?
This analysis provides an overview of key considerations if you suspect you’re being targeted. It covers the group's operational methodology, key TTPs, and specific intelligence that indicates active targeting of major corporations.
Announcing targets
The threat posed by this group is very real. Intelligence from Telegram and Silent Push suggests that a major UK mobile service provider is now a target.
The identification of the domain sts-<service_provider>[.]com serves as a direct indicator of attack – pre-attack intelligence demonstrating premeditated targeting.
Analysis of the domain reveals:
- Naming convention: The sts-[companyname].com format is a known pattern used by Scattered Spider to impersonate a security token service (STS) or single sign-on (SSO) portals.
- Infrastructure: The domain's hosting and association with the group's known phishing infrastructure align with its established operational patterns.
The creation of this bespoke infrastructure signifies a clear intent to execute a credential harvesting campaign specifically against those businesses’ employees, representing the initial phase of its broader attack plan.
Posts on a Telegram channel potentially owned by the hacking groups discussed their desire to attack a major UK Telco. The channel is no longer live, and there’s a discussion around whether this post is legitimate.
While it can’t be 100% verified that it comes from Scattered LAPSUS$ Hunters, the channel has a consistent posting history. It’s also worth noting that these channels never last very long, given that they're banned by Telegram and new channels are regularly created.
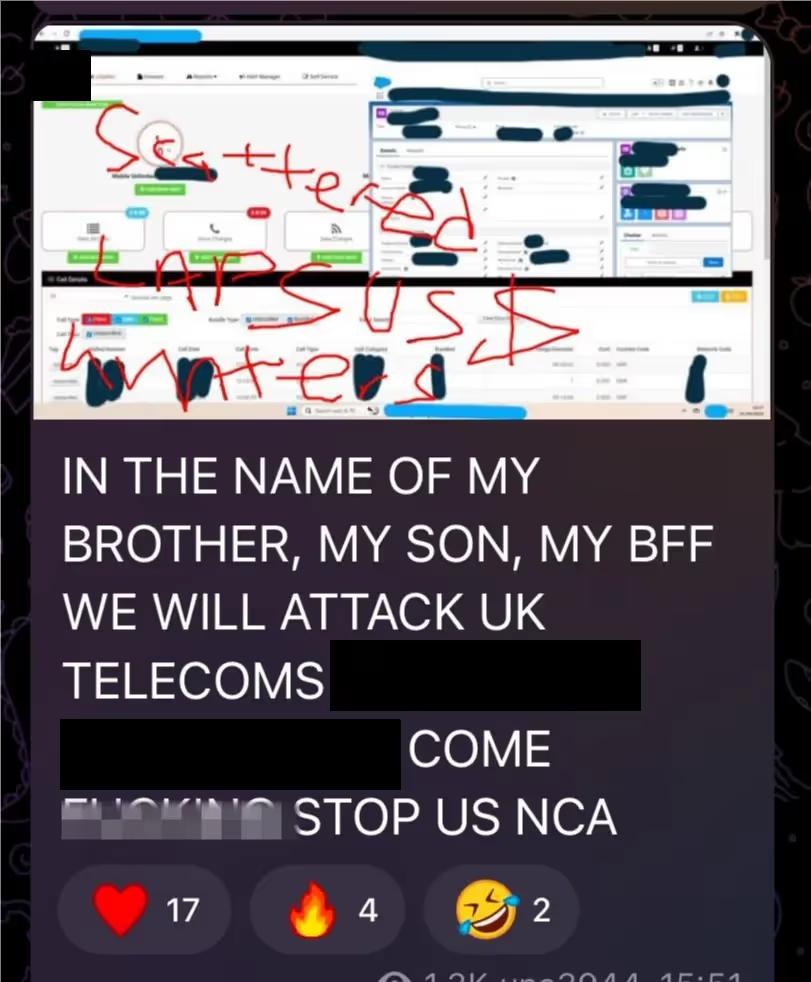
However, this gives organizations like this an opportunity to ready their defenses in case this is a real threat.
A response framework: Countering a targeted threat
When intelligence indicates that an organization is being specifically targeted by a sophisticated threat actor like Scattered LAPSUS$ Hunters, a swift, multi-faceted response is critical. It can
The goal is to move from a reactive posture to an intelligence-led, proactive posture that enables effective defense. Your immediate actions should be organized across four key workstreams.
1. Intelligence-led proactive defense
The first priority is to understand the adversary and harden your defenses based on their known playbook.
- TTP collation: Immediately collate all known TTPs associated with the threat actor. This involves analyzing their preferred methods for initial access, lateral movement, and data exfiltration.
- Enhanced threat hunting: The security operations center (SOC) should initiate enhanced threat-hunting campaigns specifically looking for indicators of attack matching the group's TTPs, such as the use of certain remote monitoring and management (RMM) tools or unusual identity-based activity.
- Intensified intelligence scanning: Task your cyber threat intelligence teams, including dark web analysts, to conduct deep and dark web monitoring for any mention of your organization, executives, infrastructure, datasets, or intellectual property. The search should include chatter on criminal forums, marketplaces selling alleged credentials, and any new phishing infrastructure being stood up.
- Vulnerability and patch management review: Conduct an urgent review of your patch management status to ensure any known vulnerabilities leveraged by the group are remediated, closing potential windows of opportunity.
2. Strategic collaboration and information sharing
No organization can defend in isolation. It’s vital to utilize the collective knowledge of the security community.
- Engage with national agencies: Coordinate with the National Cyber Security Centre (NCSC) in the UK or the Federal Bureau of Investigation (FBI) in the U.S, as well as other relevant law enforcement agencies. The objective is to share your intelligence and receive any classified or sensitive information they may hold regarding the threat actor's current campaigns.
- Activate industry networks: Engage with your industry's computer emergency response teams (CERTs) and information sharing and analysis centers (ISACs) to share your findings and gather intelligence from peers who may be observing similar activity.
- Establish response cadence: Create an internal “threat response” working group, with a regular cadence of calls to ensure all teams (SOC, CTI, IT, internal and external comms) are coordinated in their planning and execution.
3. Reinforcing the most important aspect – humans
Given this group's focus on social engineering, strengthening your human defenses is a critical and immediate priority.
- Targeted security awareness: Issue a security awareness bulletin across the entire organization. This communication should focus specifically on the TTPs of vishing (voice phishing), phishing, and smishing, providing clear examples of what to look for.
- Reinforce security hygiene: We would reiterate the importance of basic security hygiene, such as not reusing passwords and being cautious of unsolicited requests for information.
- Clarify legitimate domains: To counter the group’s use of typosquatted domains, the communication should explicitly state the only legitimate domains used for your SSO or STS logins, and advise staff to treat any other variation as malicious.
4. Controlled and effective communication
Your communication strategy should be carefully managed to raise alertness without causing panic.
- Stakeholder briefings: A select group of key stakeholders should be briefed on the specifics of the threat. Avoid widespread internal communication that you are “under attack”.
- Organizational alert: A general communication should be sent to all staff stating that everyone is operating in a heightened threat environment.
- Reinforce reporting and vigilance: Strongly reinforce the process for reporting anything suspicious, no matter how small. You should emphasize the need for increased vigilance, making it clear that every employee is a vital part of your collective defense. Make the message simple: if you see something, report it immediately.
Operational methodology: Identity-centric intrusion
The core philosophy of Scattered LAPSUS$ Hunters is a departure from traditional network exploitation. Its approach is best described as “log in, not hack in”. It focuses on compromising legitimate user identities and accounts to circumvent security controls.
This strategy effectively bypasses traditional perimeter defenses by targeting the human element and the organization's identity and access management (IAM) infrastructure.
Tactics, techniques, and procedures (TTPs)
Initial access: Social engineering and credential harvesting
The group's primary vector for initial access is voice phishing (vishing). Operators, typically native English speakers, have demonstrated high proficiency in impersonating employees during calls to corporate IT help desks.
They leverage pre-acquired personally identifiable information (PII) to successfully navigate security verification questions and persuade support staff to perform actions such as password resets.
These vishing attacks are often preceded by sophisticated phishing and SMS phishing (smishing) campaigns. The adversary utilizes typosquatted domains mimicking corporate portals (e.g., SSO, VPN) and employs advanced phishing kits like Evilginx.
This tooling enables machine-in-the-middle attacks that capture not only credentials but also session cookies, thereby bypassing multi-factor authentication controls.
Techniques for multi-factor authentication (MFA) evasion
Where direct credential harvesting is insufficient, the group employs several methods to defeat MFA:
- MFA fatigue: The adversary inundates a target's device with a high volume of MFA push notifications, intending to induce the user into accidentally or impatiently approving a malicious login prompt.
- SIM swapping: A social engineering attack directed at a target's mobile service provider. The objective is to port the victim's phone number to an attacker-controlled SIM card, granting them the ability to intercept SMS-based, one-time passcodes (OTPs) used for authentication and account recovery.
- OAuth abuse: Attackers trick employees into granting permissions to a malicious third-party “connected app”. This provides the adversary with a persistent OAuth access token, enabling API-based data access without requiring the user's password.
Post-exploitation: “Living off the land” and data exfiltration
Upon gaining network access, the group prioritizes stealth and operational speed. It heavily favors “living off the land” (LotL) techniques, using legitimate and allowlisted software – such as RMM tools (AnyDesk, TeamViewer), PowerShell, and native cloud administration consoles – to blend with normal administrative activity.
The group’s primary objective is the mass exfiltration of high-value data. After conducting internal reconnaissance of systems like Active Directory, it targets corporate data repositories, including SharePoint sites, source code databases, and cloud data warehouses (e.g., Snowflake, Amazon S3). It has been observed using enterprise backup software like Veeam to conduct large-scale, covert data transfers.
Furthermore, the group actively engages in defense evasion by disabling or uninstalling endpoint detection and response (EDR) agents. In an advanced counter-incident response tactic, it has been known to monitor a victim's internal communications (Slack, Teams) to anticipate and evade remediation efforts.
Insider threat recruitment
A notable and high-impact vector, pioneered by LAPSUS$, is the active recruitment of malicious insiders.
The group has publicly solicited employees of target companies via platforms like Telegram, offering financial compensation in exchange for corporate credentials or remote access. This strategy presents a significant non-technical risk, bypassing established security perimeters entirely.
Explore more
Whether you’re in cyber, crisis management, or operational leadership, visit our latest content and exercises to learn more about the tactics and tools behind Scattered Spider:
Exclusive content for Immersive customers:
- Lab – Scattered Spider and Dragonforce: Campaign Analysis
- Lab – Threat Actors: Scattered Spider
- Workforce Scenario – Social Engineering Techniques
- Crisis Sim – Responding to a Scattered Spider Attack
These resources are designed to help your teams be ready, not just to understand the threat, but to prove and improve how you’ll respond when it matters most.
References:














Ready to Get Started?
Get a Live Demo.
Simply complete the form to schedule time with an expert that works best for your calendar.





.svg)







