I never really thought about just how exposed the person-in-the-middle is during a cyber attack – that is, until I heard about the Royal Mail ransomware attack. On January 11, 2023, the international division of the UK postal service Royal Mail publicly disclosed shipping disruptions caused by a ransomware attack. Besides the obvious hardship caused by delayed mailing services, one person in particular, the Royal Mail International negotiator, had his worst day shared with many others on the internet.
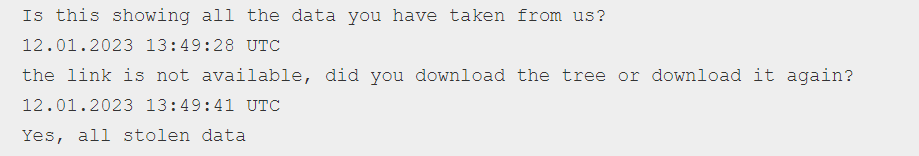
For whatever reason, these attackers decided to publish the transcript of their conversation with the negotiator. When reading through the transcript, the Royal Mail International negotiator pleads for a reduction in the amount they need to pay, the release of crucial files to help critical medical shipments, and patience as his upper management tries to work out what to do.
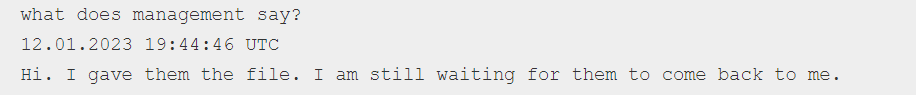
This means that anyone in this position has to worry about successfully negotiating a resolution and the downstream implications of having the entire exchange released in the public domain. Now think about what would happen if your typical day-to-day business conversations were made public; your discussions with a tardy vendor, performance reviews, or salary negotiations – all shared on the internet! It just doesn’t get any more personal than this.

This particular situation exposes another issue for the negotiator; how do they determine the actual intent of the attacker? Highly personal (human) motivations also guide that attacker. The negotiation would surely go better if the victim of the attack understood whether the attacker was a nation-state threat actor, in it for personal gain, a thrill seeker, or on a mission through hacktivism.
All of this means that an organization deciding how to develop or strengthen its cyber resilience strategy has to consider the human element – the person(s) in the middle – in every aspect of its training and preparation, both internally and externally. Training covering everything from a reverse-shell attack to whether we are prepared to have our ransomware negotiation – whether successful or not – in the public domain should be a priority.
At Immersive Labs, we provide people-centric cyber resilience at scale. We built our business on the fact that cybersecurity is about people. All the technology in the world doesn’t matter if your people and teams aren’t equipped and exercised to address the challenges facing today’s cybersecurity practitioners.
To accomplish this, we’ve developed a cyber resilience platform that extends to every level of an organization so you can assess, build, and prove your cyber readiness. Our hands-on labs feature highly-technical labs covering all aspects of cybersecurity, including offensive, defensive, cloud, and application security. Leveraging gamification and live environments, users can learn topics ranging from basic security to malware reverse engineering and advanced threat hunting.
Immersive Labs organizational exercises cover the latest cyber threats (including the Royal Mail scenario) and provide cloud-based Crisis Simulations for Boards, executives, and crisis management teams. Using realistic exercises to measure and improve response ensures that teams (and individuals) are prepared when a cyber crisis emerges. With an assortment of out-of-the-box scenarios, these exercises deliver in-depth, real-world simulations.
We also provide technical exercises that are enabled using cyber range technology. Your security teams can collaborate using real-world scenarios by replicating daily experiences using pre-configured, task-based technical simulations. We also deliver custom cyber range capabilities, so you can more closely replicate your production environment. Our cyber range technology allows your teams to practice and prepare for cyber attacks safely and without compromising security.
To learn more about how your organization can achieve cyber resilience, you can schedule an appointment here.


