Can You Trust Single Sign-On? A Novel Technique for Stealing Credentials
You open your work laptop ready for another day at the office. You see a pop-up urging you to log in to your Microsoft account. But how do you know this pop-up is legit?
The content team at Immersive Labs has developed and tested a sample phishing payload, where attackers take advantage of application mode’s characteristics on Chromium-based browsers to launch realistic popups and have some interesting findings.
Based on the original work of mr.d0x, attackers can use these malicious pop-ups to request credentials from users, all while seeming like the usual single sign-on (SSO) login page.
That’s why this attack is so dangerous– especially in environments where users are conditioned to enter credentials into such SSO pop-ups routinely. Once an attacker has your credentials, it’s easy for them to gain further access into your system and even fully compromise it.
What should I look out for?
Application mode launches Edge or Chrome in a window like normal, but with some major differences – there’s no address bar or other usual navigation features, and no visual indicators of security that users are taught to trust, such as known URL addresses or the SSL padlock
Because of the lack of these features, it’s difficult to confirm the true identity of the website that’s presented to you. But, with a bit of persistence, it’s possible to confirm the webpage’s identity in DevTools (available via the right-click menu).
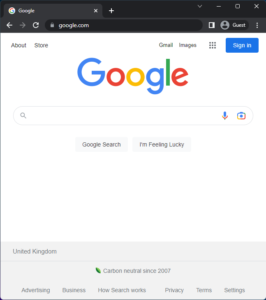
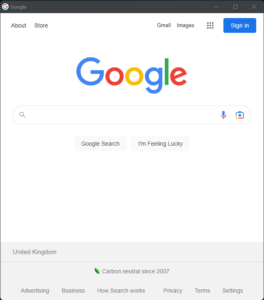
Compare the two images. The first is a regular website in the browser, the second is in application mode.
Advanced detection
Aside from the indicators of compromise (IoCs) that result from payload delivery (via a phishing attack or a user accessing a newly created phishing domain), the method used to start a browser has some obvious static detections. These should stand out in environments where users aren’t routinely opening pages or applications using the same method.
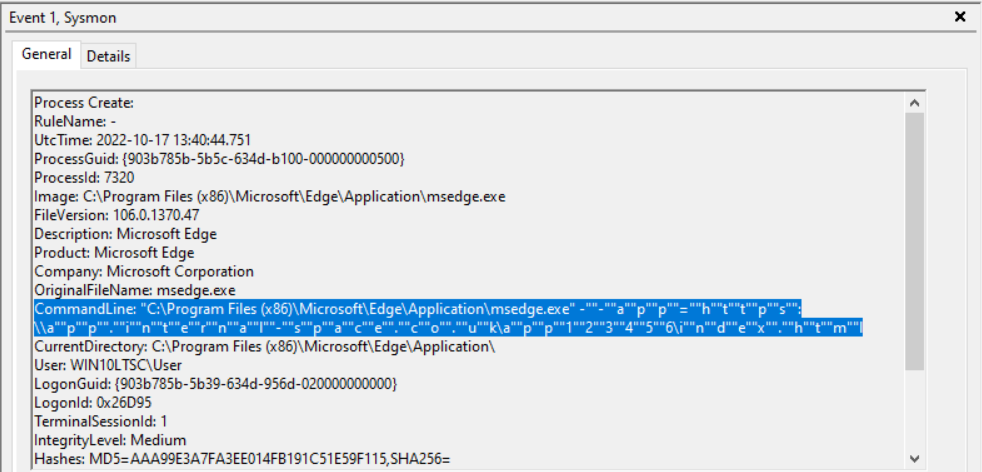
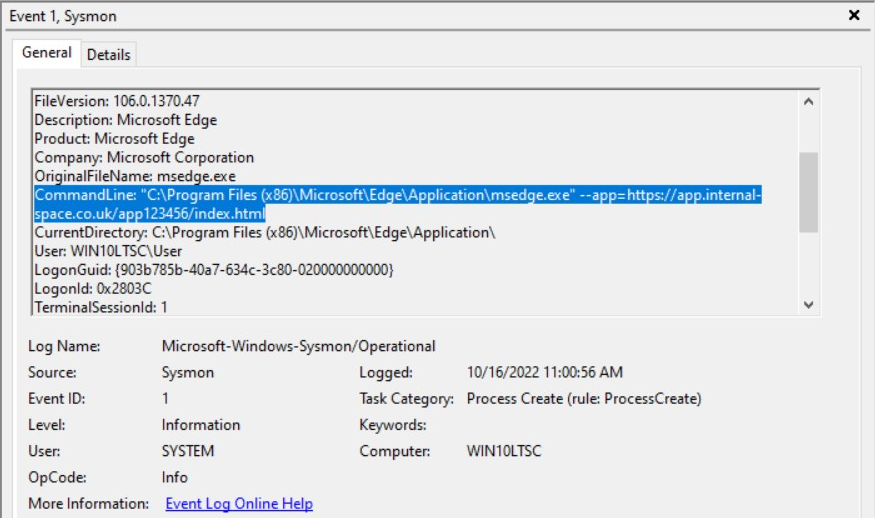
The screenshot above shows an extract from the Sysmon section of Windows Event Log. As you can see, the highlighted text uses the app flag in the command line arguments. Depending on your alerting platform, this should be trivial to configure detections for.
Keep in mind that the attacker could also choose to use other command line flags to open a remote or locally hosted payload. During our testing, we used the following permutations (but it’s likely there could be more):
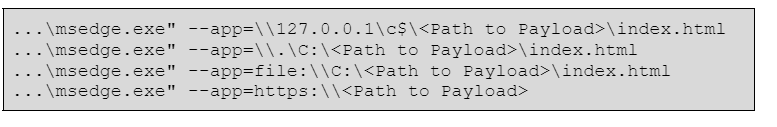
Additionally, it’s likely that attackers will choose obfuscation techniques to bypass brittle detections used by defenders, such as those discovered via static analysis or from process start events. The screenshot below gives a simplified example of erroneous characters that could be added to break a static signature, but still allow for execution:
In this case, detection very much depends on the defender’s SIEM capability to rationalize or identify whether command line obfuscation is present or used in the attack chain.
How do attackers perform this technique?
Check out the GIF below to see how this type of attack is employed. An attacker uses a crafted link (LNK) file to launch the Edge browser in application mode, which in turn opens a remotely-hosted phishing site.
Interestingly, the whole attack must be performed on the originally opened webpage, with no navigation to a subsequent page. This allows the JavaScript window.close() method to close the existing window in modern browsers once the user completes the fake authentication process.
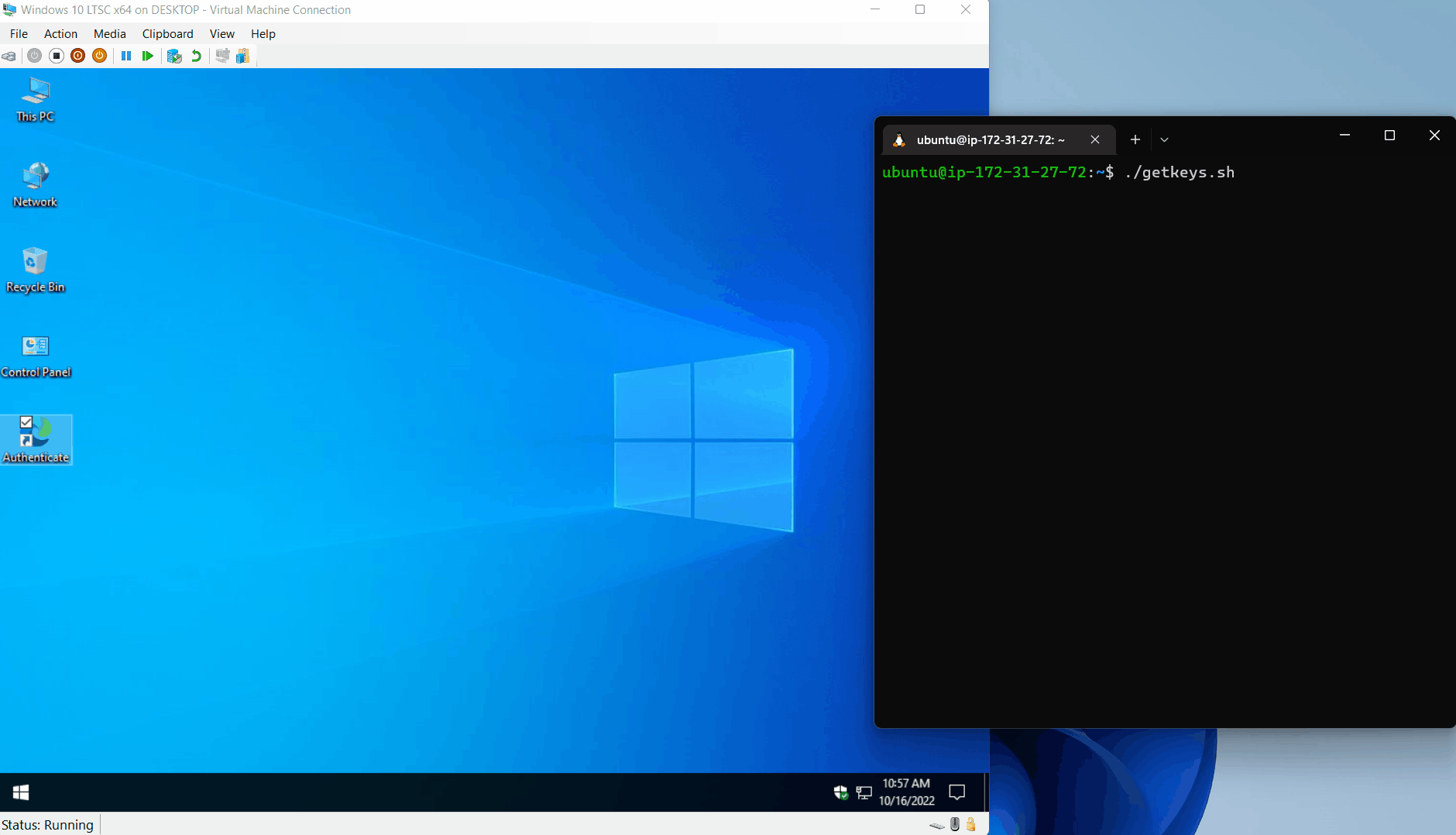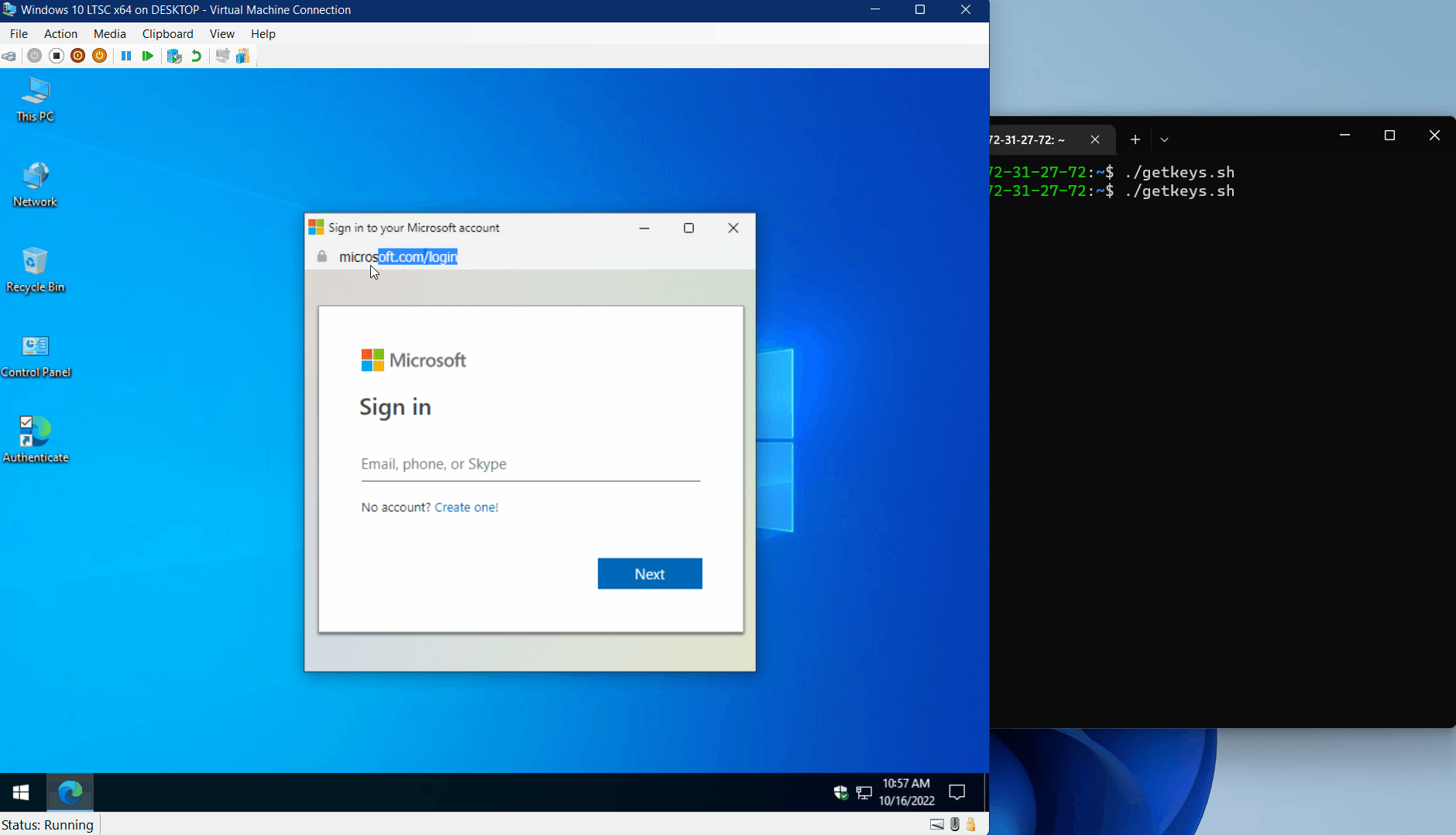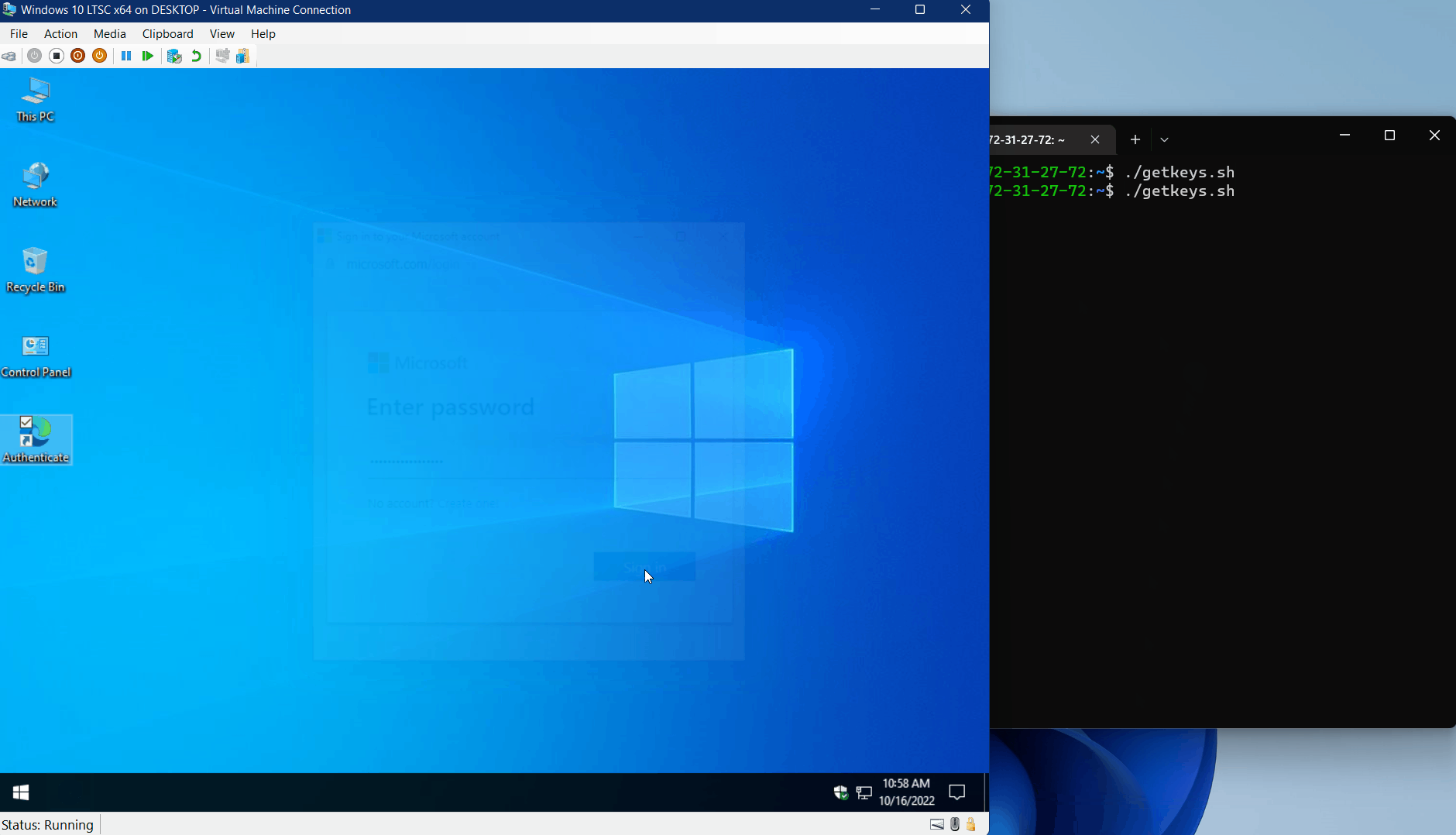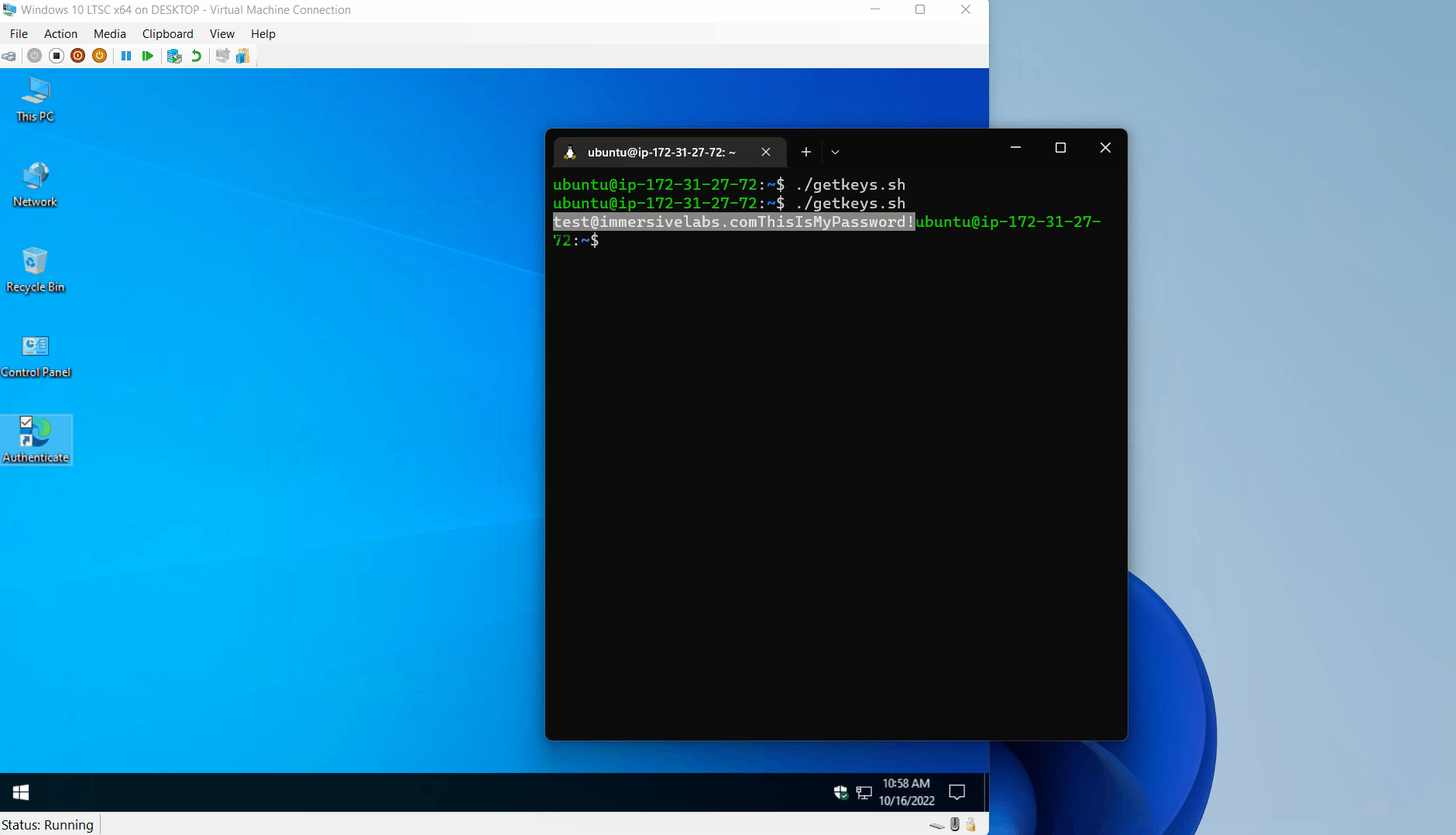
An obvious next step is for an attacker to make use of a simple JavaScript keylogger in the page to capture the user’s input as they type. This information can be retrieved from the server HTTP access log, but an attacker with the time to engineer a more elegant solution could build infrastructure to do so at scale, differentiate between different targets, or use other protocols such as DNS rather than HTTP(S) to exfiltrate keylogs as they’re typed.
It’s also worth noting that this technique could be combined with other payloads or methods. For example, they could use a malicious document or drop the entire payload to disk and access it by the browser locally, instead of hosting the phishing site remotely.
Final thoughts
Although a relatively simple technique on the surface, using application mode to further enhance the legitimacy of phishing attacks may be potent in enterprise environments – especially where users routinely make use of SSO operations for desktop applications and services.
Protection against credential exfiltration or further attacks in part lies in current security best practices, including control over whether users can visit untrusted domains and traffic inspection. In addition, defenders should consider adding static detections and evaluating whether their existing SIEM solution can rationalize or detect command line obfuscation techniques.
Book a demo with Immersive Labs today to learn about how we can help you improve your people-centric cybersecurity.