Security awareness and behavioral change should be inexorably linked in any cyber resilience program – but for most, it isn’t. Organizations need effective strategies to educate their employees and positively influence their behavior. But even this is not enough. They also need an effective way to understand and assess the current risks that their organization carries. Traditional awareness programs focused on training completion rates are not sufficient, failing to reveal true risk. Instead, we need to enable organizations to focus on effectively measuring behavioral risk. This blog delves into our approach and demonstrates how we integrate behavioral science, gather crucial data, and employ scenario-based learning to empower organizations and individuals, drive change, and enhance security.
Behavioral science: a cornerstone
We recently introduced Workforce Exercising, a key component of the Immersive Labs platform, to fill the gap left by typical security awareness training by embracing behavioral science techniques. It engages an organization’s workforce with relatable content using scenario-based exercises to baseline, assess, and upskill on crucial security behaviors – and then educates with targeted, on-demand labs. From the beginning of our Workforce Exercising journey, we recognized that understanding human behavior is crucial in creating effective security solutions. Behavioral science, which delves into how people make decisions and their actions, became the cornerstone of our approach.
The four pillars: a comprehensive strategy
Our strategy revolves around four key areas: understanding behavior, data-driven reporting, our security hygiene compass, and tailoring/customization. These areas ensure a comprehensive approach to security and behavioral change.
- Understanding Behavior: At its core, our product focuses on applying behavioral science principles to positively influence security behaviors. This starts with understanding why people act as they do and giving them the skills and knowledge they need to behave securely.
- Data-driven Reporting: Assessing the impact of interventions has always been a challenge with traditional awareness campaigns. Our product starts with establishing a baseline of current security behaviors supported by continued data-driven reporting, enabling you to identify gaps, monitor change over time, and target the most needed interventions.
- Using the Security Hygiene Compass: This data-driven tool was designed with behavioral insights at the forefront. It guides organizations through the intricate and complex landscape of security behavior, enabling you to identify potential risks across a range of areas in a single exercise.
- Tailoring and Customizing: Recognizing that one size doesn’t fit all, we empower users to customize our product to suit their unique needs and contexts. Customization ensures relevance and effectiveness across diverse audiences.
Integrating behavioral science: a fundamental approach
Our journey into integrating behavioral science began at the product’s inception. The first step was understanding the security behaviors we targeted and how they related. We created a “heat map” to visualize these behaviors and identify areas of concern within organizations. This map provided a solid foundation for our endeavors.
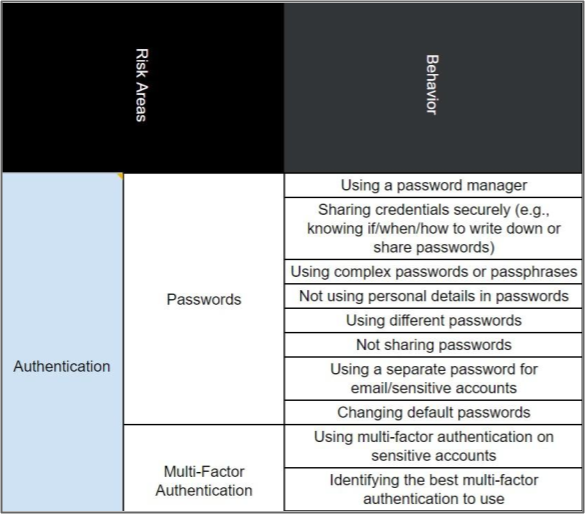
Our product’s primary focus revolves around understanding and influencing behavior, whether that involves supporting organizations to change behavior or gaining a deeper understanding of what behaviors could present a problem in the first place. To facilitate this, we organize behaviors hierarchically. Starting with overarching topic areas (e.g., authentication, moving down into subcategories (e.g., passwords), and then drilling down into specific actions or behaviors related to these (e.g., not sharing passwords with others, not reusing them across multiple accounts, not including personal information in passwords, etc.).
This hierarchy helps us understand the behaviors associated with various risk areas, providing a structured approach to addressing security concerns.
Assessing behavior and gathering data
Measuring security behavior directly is time-consuming, costly, and has implications for employee privacy. So, we use the next best thing, employing scenario-based assessments to assess participants’ judgments and gauge their understanding of what they should do in specific situations. This approach has been used effectively in multiple disciplines, including medicine and general personnel selection. This approach also allows us to measure participants’ confidence in their decisions in a ‘safe’ space.
Scenarios play a pivotal role in our assessments. They provide learning through stories and enable the creation of narratives, contexts, and responses that people can relate to. They incorporate multiple response options covering a range of actions that could be taken, reducing the likelihood that participants will simply choose the most obvious answer. More response options encourage participants to think critically, particularly when distractor options are included (i.e., responses that are okay but may not be the most useful or relevant). This adds depth to our assessments and ensures robust and nuanced data collection.
The Security Hygiene Compass: guiding organizations to success
Our “Security Hygiene Compass” is a robust assessment framework designed to help organizations easily identify gaps and strengths across various security behaviors. Its development involved a rigorous process based on situational judgment tasks and Delphi methodology. Subject-matter experts and user testing played a crucial role in refining and validating the compass, ensuring its effectiveness in guiding organizations to security success.
Learning quality: scenario-based learning for effective education
Ensuring the quality of learning is another critical aspect of our approach. We employ scenarios to engage participants with a narrative and help them make decisions within a safe environment. Stories within these scenarios facilitate learning by allowing participants to connect emotionally and cognitively with the content.
Immediate ‘in-the-moment’ feedback within scenarios enhances the learning experience. It helps participants understand why an answer is right or wrong. Key takeaways and clear next steps encourage participants to take action based on what they’ve learned and address gaps in their knowledge. This approach educates and empowers individuals with a route to upskilling.
Customizable feedback: tailoring the experience
Our product allows users to customize their experience, including feedback within scenarios. Users can turn this feature on or off, aligning with their preferences and requirements. Furthermore, users have the option to customize the content of feedback to match their own organizational policies and suit their specific needs. While feedback is customizable, the fixed grading terms, such as “great,” “good,” “weak,” and “okay,” provide a consistent way to group and assess.
Mapping behaviors to scenarios
In practical terms, integrating behavioral science, data collection, and scenario-based learning results in scenarios carefully mapped to specific behaviors. These scenarios are categorized and tagged to risk areas and behaviors, ensuring a comprehensive assessment of security behaviors.
Our approach to driving behavioral change and enhancing security in Workforce Exercising is holistic, emphasizing the importance of understanding, influencing, and assessing behaviors to create a secure and informed environment. Our commitment to customization ensures that our product aligns perfectly with the unique needs of each user or organization, making it a powerful tool for achieving your security goals.
Learn more about Workforce Exercising here.


