Exploring methods to ensure DORA compliance?
Learn how Immersive Labs helps organizations meet and sustain DORA compliance needs.

The Digital Operations Resilience Act (DORA) was published in the Official Journal of the EU on 27 December 2022. This includes a Regulation and a Directive on digital operational resilience for the financial sector. This Regulation is now in force and will apply in full from January 2025.
DORA applies to all financial institutions in the EU to address digital operational risk in the financial sector in a consistent manner in one single legislative act.
It introduces targeted rules on:
- Information and Communication Technology (ICT) risk management
- ICT–related incident management, classification and reporting
- Digital operational resilience testing
- Managing ICT third-party risk (including the introduction of an oversight framework for critical ICT third-party service providers)
- Information and Intelligence Sharing
The European Supervisory Agencies (ESAs), the European Banking Authority (EBA), the European Insurance and Occupational Pensions Authority (EIOPA), and the European Securities and Markets Authority are jointly leading the development of technical standards as required by the DORA Regulation. These were delivered in two tranches (click the link for more details).
Tranche 1: Published in June 2023
- Further specify required elements of financial entity’s risk management framework, and, where applicable, a simplified risk management framework
- Further specify the criteria for the classification of ICT-related incidents, materiality thresholds for major incidents, and significant cyber threats
- Further specify outsourcing policy on contractual arrangements with ICT service providers supporting critical or important functions
- Establish standard templates to be used in the register of information in relation to all contractual arrangements on the use of ICT services provided by ICT third-party service providers.
Tranche 2: Published in December 2023
- Establish forms and procedures for financial entities to report a major ICT-related incident and to notify significant cyber threats
- Specify further elements for financial entities to determine and assess when sub-contracting ICT services supporting critical or important functions
- Further specify the details of advanced testing of ICT tools, systems, and processes based on threat-led penetration testing (TLPT) – including criteria to be used to identify those financial entities that are required to perform TLPT
- Harmonise conditions enabling the conduct of oversight of ICT service providers which are designated as critical.
Immersive Labs can positively help with key metrics and requirements of the DORA initiative.
- Deployment frequency
- Lead time for changes
- Time to restore service
- Change failure rate
- Information and Intelligence Sharing
Here’s how Immersive Labs can contribute:
Deployment Frequency
Measure how often code is deployed to production. High deployment frequency is often associated with better organizational performance.
Hands-On Labs – Realistic environments for teams to practice and learn how to automate deployment processes, enabling experimentation with various strategies, tools, and configurations in a controlled setting. Boost confidence and skills for frequent code deployment.
Application Security – Simulate real-world deployment scenarios, including dealing with dependencies, scaling issues, and environmental variations. Identify and address potential challenges affecting deployment frequency.
Lead Time for Changes
This is the time it takes to go from code commit to code successfully running in production. Shorter lead times are generally associated with more efficient and streamlined development processes.
Application Security – Work with simulations of end-to-end workflows, from planning to secure coding to deployment. Teams can optimize and streamline these workflows, identifying bottlenecks and inefficiencies that hurt lead times. Implement improvements that reduce lead times.
Hands-On Labs – Train using the latest in automation tools and practices. Automation significantly contributes to reducing lead times, and teams can use labs to master the automation of testing, integration, and deployment processes.
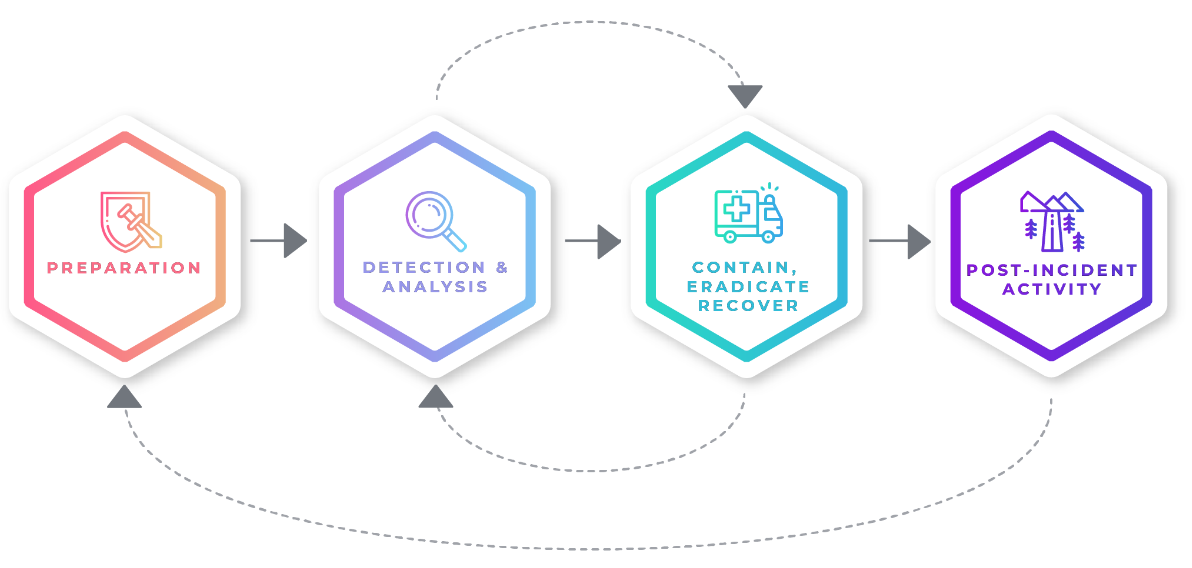
Time to Restore Service
Interact with and learn about the newest threats or vulnerabilities quickly. New content comes out just as often as new vulnerabilities are discovered.
Cyber Threat Intelligence – Learn to monitor and share information on the latest vulnerabilities with hands-on labs.
Real World Playground – Focus your efforts on web application threats and vulnerabilities.
Change Failure Rate
This metric looks at the percentage of changes that result in a failure, such as a defect or service outage. A lower change failure rate indicates more reliable and stable releases.
Application Security – Immersive labs provide testing and validation exercises in a controlled environment for teams to thoroughly review changes before deploying.
Hands-On Labs – Collaborative learning fosters a learning environment where cross-functional teams can work together to understand the impact of changes on different components. This collaborative approach enhances communication and coordination, reducing the likelihood of failures due to miscommunication or team misunderstandings.
Information and Intelligence Sharing
Interact with and learn about the newest threats or vulnerabilities quickly. New content comes out just as often as new vulnerabilities are discovered.
Cyber Threat Intelligence – Learn to monitor and share information on the latest vulnerabilities with hands-on labs.
Cyber Workforce Resilience
Immersive Labs provides a dynamic, experiential learning platform that enhances organizational cybersecurity capabilities. Our people-centric approach empowers organizations to fulfill various DORA requirements but also goes beyond by offering additional cybersecurity functionalities.
The Immersive Labs Platform – Leverage our approach to people-centric cybersecurity to assess, benchmark, build, and prove cyber resilience.
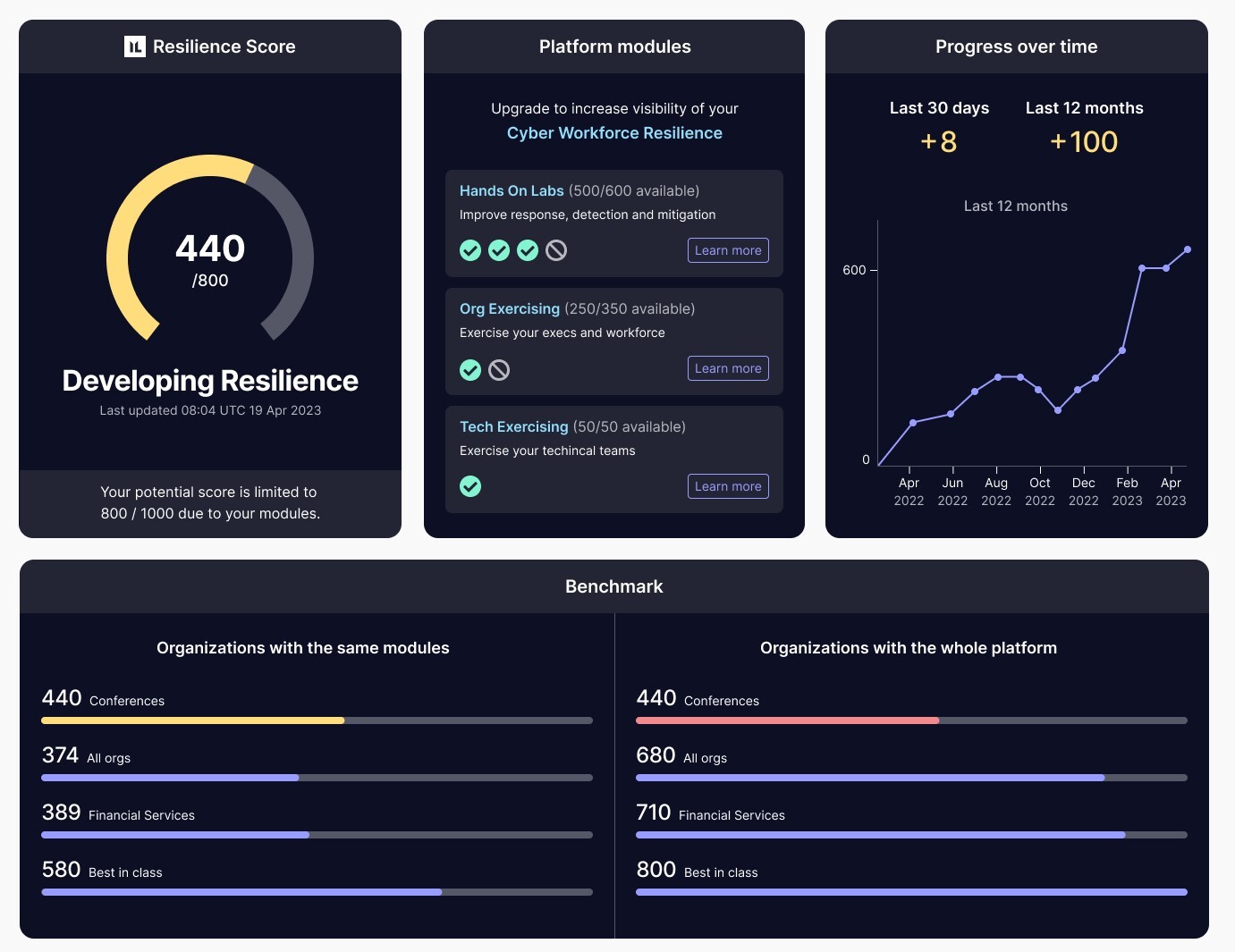
Resilience Score – Engage advanced statistical methods to evaluate, compare, enhance, and substantiate resilience through a transparent, data-driven approach.*
Evidence-Based – Employ granular performance data and alignment with security frameworks, including MITRE ATT&CK.
Workforce Exercising – Understand and prove your overall cyber resilience covering eight key security risk areas