Hackers have first-move advantage – that’s why defenders should learn like they do

Reconfiguring Cyber Defense:
Learning Like Threat Actors to Stay Ahead
If threat actors didn’t innovate, we would have already won. It’s their ability to imagine new ways to hurt us, and then execute them at speed, that has left us chasing shadows. Add lawlessness to the mix, and it feels like bad guys are almost always ahead.
But why is that? An attacker’s first-move advantage clearly comes down to their rapid innovations, meaning security teams always have to operate reactively. Like forest fires, cyber-attacks are devastating and unpredictable; and like firemen, defenders can only race to the scene. But by the time they arrive, the damage is usually done.
In fact, it’s this conundrum that led Immersive Labs to intelligence-led learning. We wanted to reconfigure the threat landscape to give security teams a fighting chance, because if they are forever reacting, they cannot possibly thwart cybercrimes. We knew that to make up ground, security pros had to learn like threat actors.
Take open-source software Tor, for example, which the US Naval Research Laboratory set up to secure its intelligence communications in the 90s. Criminals didn’t sit around admiring this innovation. They got to grips with it and used it to their advantage – something that ultimately led to the creation of the dark web.
Blurred lines
All cyber-skilled individuals, good and bad, have the same qualities: they learn fast, they persevere, and they dare to tread boundaries. But most of all, they want to innovate.
The problem when upskilling the good guys has always been this: how do we keep them at the cutting edge of cybersecurity while staying legal? At Immersive Labs, we want our users to innovate as fast as the criminals. That’s why we insist on building content that incorporates real threat intelligence, real tools and real techniques.
Threat intelligence is about helping defenders to think like hackers. It’s about understanding the adversary’s methods and putting measures in place to stop them hurting you. The challenge for defenders will always be keeping pace, which is why the focus should be on reducing the time between the attacker’s strike and your reinforcements going up – the Mean Time to Learn.
An example of how we’re reducing Mean Time to Learn comes via the WannaCry virus. We built a lab that allows users to handle the malware in a sandboxed environment, so they can activate it, watch it spread, and analyze it forensically – all with complete peace of mind. This lab was on our platform within six hours of WannaCry hitting the NHS.
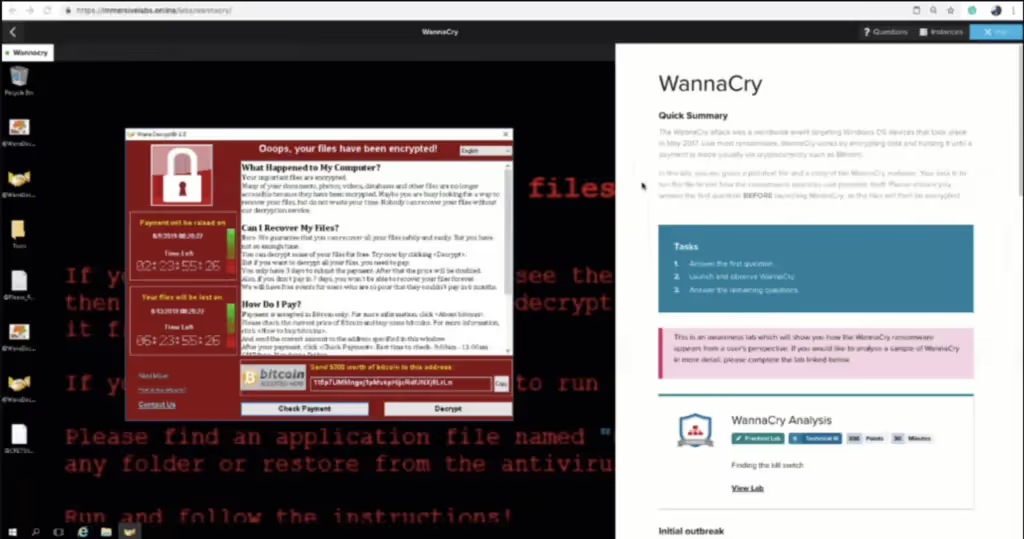
Keeping pace is not about teaching someone about ethical hacking or reverse engineering or pentesting. It’s asking, can we learn about the threat that’s going to hit our organization two hours before it hits? That’s the key – it’s asking how we can learn like hackers and build awesome defenders with the right motivation.
Where traditional training fails
The problem with traditional cyber training is that courses are often months out of date before instructors have even delivered them. They teach techniques like pentesting but not the real-world skills you need to stop an attack in a job. It’s a rigid learning style; most hacker-types don’t want to sit in a classroom from nine to five to acquire expensive certifications, which essentially mean you’ve done a hundred multiple-choice questions at the end of a five-day course.
Classrooms are relics of the late Industrial Revolution, when we first began arranging desks in rows so that information could be passively absorbed. Over a century later in 2019, they should not be our primary mode of education. This is especially true when it comes to technical subjects, which are best taught through facilitation rather than instruction. In a classroom learners are rarely, if ever, of identical abilities, meaning the group can only go as fast as the least technical person. It’s inefficient to say the least.
Hackers clearly don’t learn best through classroom training – and they certainly aren’t inspired by paper certificates. There is a better way, though: rapid access to relevant, hands-on learning experiences where, and when, defenders need them. You can start building a realistic strategy for training security pros with our Ultimate Cyber Skills Strategy Cheat Sheet, which is teeming with practical, easy-to-follow steps.
Trusted by top
companies worldwide














Ready to Get Started?
Get a Live Demo.
Simply complete the form to schedule time with an expert that works best for your calendar.





.svg)
.webp)









.webp)


