In the intricate landscape of cybersecurity, the ability to dissect and understand the inner workings of software – malicious or otherwise – is paramount. Enter reverse engineering: a disciplined approach that enables professionals to identify vulnerabilities and anticipate potential threats.
By mastering the principles of reverse engineering, cybersecurity teams can enhance their proactive defense mechanisms, offering unparalleled insights into the tactics and strategies of adversaries. From an exploitation perspective, teams can ensure safer computer systems for everyone, and improve an organization’s strategic posture in an increasingly complex cyber world.
At Immersive Labs, we believe hands-on experience trumps theoretical knowledge. There’s no better way to sharpen your skills than by diving headfirst into real-world challenges. This blog post explores the significance of reverse engineering and some of the complex labs we’ve created to develop your skills in this highly sought-after area of information security.
Each exercise crafted by Immersive Labs is designed to stimulate your cognitive abilities, inviting you to think, analyze, and hypothesize about how to exploit these vulnerabilities or reverse engineer malware. Whether you’re a seasoned professional or an enthusiastic novice, these scenarios are complex and show you fun ways to exploit Windows and Linux processes.
Malware analysis: Darkside.dll Deobfuscation
On Thursday, May 6, 2021, Colonial Pipeline was struck by a ransomware attack. According to statements made by the FBI, the perpetrators are known as DarkSide.
This lab takes you through analyzing a variant of malware used as part of the group’s ransomware, which uses a huge array of API calls. In this lab, you’ll gain the skills to deobfuscate the malware – without ever running it.
Deobfuscating API calls in malware represents a sophisticated layer of the cybersecurity cat-and-mouse game. Malware authors often obfuscate API calls to conceal malicious activities and elude signature-based detection systems.
When these API calls are obfuscated, they appear as innocuous or nonsensical code, making it challenging for security tools to flag them as malicious. However, when deobfuscated, the reverse engineer can get a much better idea of what the code is doing.
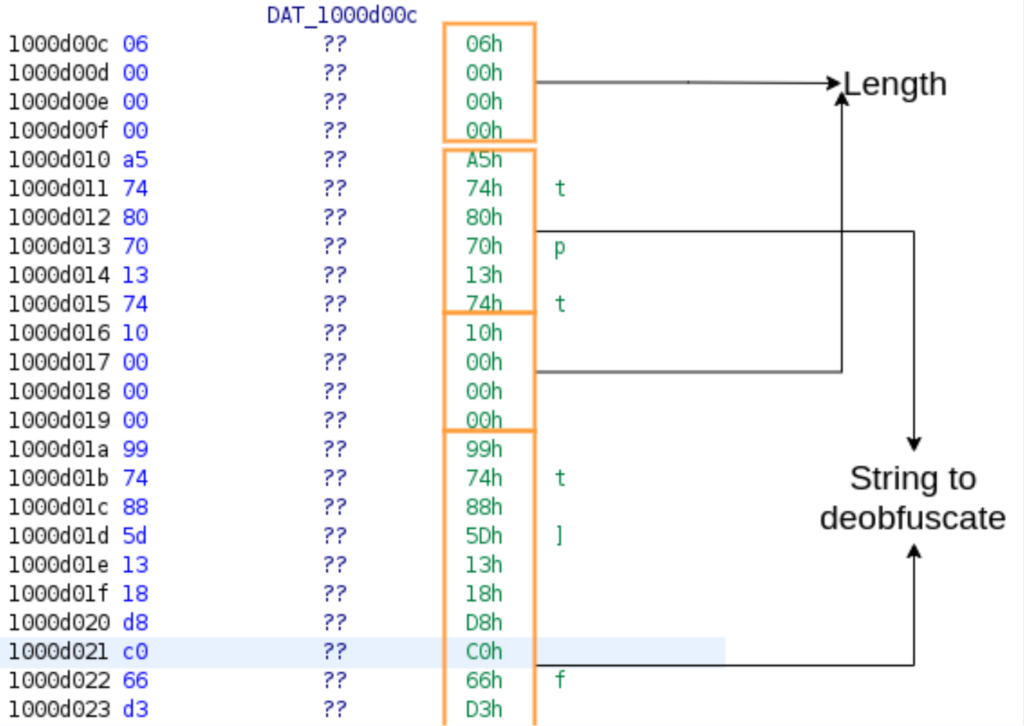
Below is an image of the obfuscated strings, which just look like some random bytes in sequence.
The deobfuscation process requires a great understanding of assembly code. You’ll use static analysis to examine the malware assembly and decompiled code without executing it to identify patterns or algorithms used in its deobfuscation process.
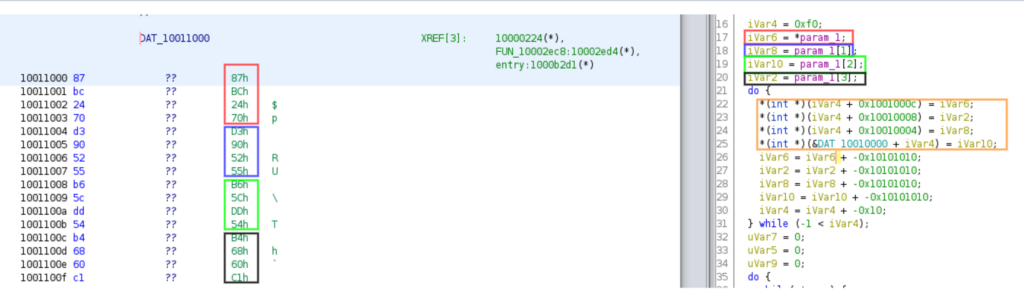
The image below shows decompiled code and how variables are matched to the data section to be deobfuscated later.
By deobfuscating these calls, cybersecurity analysts can gain a clearer understanding of the malware’s functionality, intent, and communication, enabling them to devise more effective countermeasures and defense strategies.
Linux source code Analysis: stack overflow Ep.5 – NX
Analyzing software in the Linux space, you’re faced with an exploitation puzzle. There’s an up-to-date Linux system and compiler protections, but also some software that’s still holding a stack overflow vulnerability. This exercise will redefine your understanding of Linux security for specific processes.
Exploiting a stack overflow on a Linux system, especially when the no-execute (NX) bit is set, introduces an intricate layer of complexity. The NX bit is a security feature that marks certain areas of memory, like the stack, as non-executable.
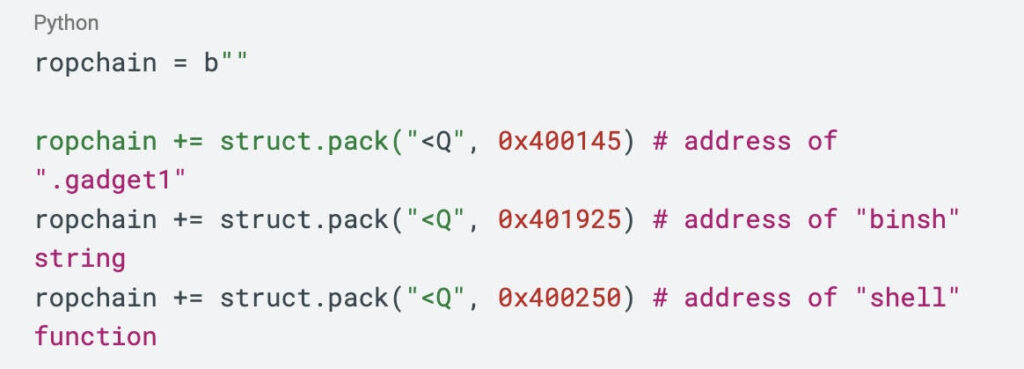
This means that even if an attacker manages to overflow the buffer and inject malicious shellcode, the system will prevent its execution. However, this doesn’t render the system impervious to attacks. In such scenarios, attackers often resort to techniques like return-oriented programming (ROP). Below is an example from the lab of a simple ROP chain used to exploit a process like this.
Instead of injecting and executing their own code, attackers manipulate the program’s control flow to execute existing snippets of code (called gadgets) in unintended sequences to achieve their malicious objectives.
Successfully exploiting a stack overflow in the presence of the NX bit necessitates a deep understanding of the system’s memory layout, binary exploitation techniques, and the application’s control flow, making it slightly more challenging.
Windows source code analysis: Heap Exploitation Ep.2 – heap overflow (practical)
Returning to the Windows domain, but with a twist – this time, you’ll analyze and exploit a heap overflow exploit lurking within an up-to-date system. Heap overflows, with their distinct complexities, offer a unique reverse engineering challenge. Dive deep, explore the intricacies of the heap, and unmask a way to exploit and redirect code execution that can lay in specific processes.
Exploiting a heap overflow on Windows systems is a sophisticated endeavor, demanding a nuanced understanding of the platform’s memory management. Unlike stack overflows, which typically involve overwriting a return address, heap overflows deal with corrupting data structures within the heap, a dynamically allocated region of memory. In a Windows environment, the heap manager governs the allocation and deallocation of memory blocks.
An attacker exploiting a heap overflow typically targets specific control data used on the heap, like function pointers or linked list pointers. By manipulating these, the attacker could redirect the program’s execution flow, leading to arbitrary code execution.
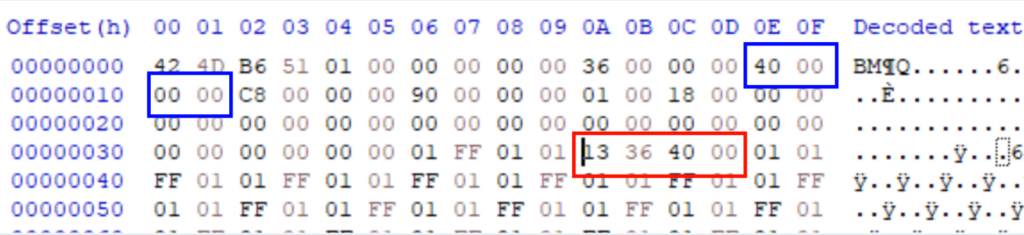
The image below shows processing software copying too much data onto the heap. Knowing which points in the heap get overwritten, you can overwrite function pointers like vtable pointers to redirect control flow when they’re called.
The image below shows the address you have code stored in that you want to execute (shown in the red box) and the amount of data you want to copy from the BMP (shown with the blue boxes).
As such, understanding and defending against heap overflows remains a priority in Windows-based cybersecurity.
When it comes to reverse engineering, we believe hands-on experience is paramount. And cybersecurity enthusiasts, professionals, and those looking to upskill can get just that with our up-to-date reverse engineering content. In these labs, you can navigate the intricacies of Windows and Linux systems, confront and dissect vulnerabilities that defy the latest mitigations, and pick apart malware to achieve an in-depth understanding of the software.
Ready to evolve? Immersive Labs awaits your next deep dive into the world of reverse engineering!
Learn more from our Resources Center.